
In this blog, you’ll learn about the fundamental aspects of HITRUST Certification, as well as receive answers to frequently asked questions about CSF HITRUST.

Here are a few variables that will affect the overall cost of PCI compliance.

Since 2014, Infosend has partnered with SecurityMetrics to meet their PCI compliance needs, ensuring their processes remain secure and their clients’ data is protected.

For 2024, our guide remains one of the best resources to use as you achieve PCI DSS compliance for your organization. It covers each requirement with clarity and thoroughness.

Check out some of the top cybersecurity conferences and events to attend in 2025 - 2026

About four years ago, Vita Companies decided to pursue HITRUST certification to differentiate themselves in the market.
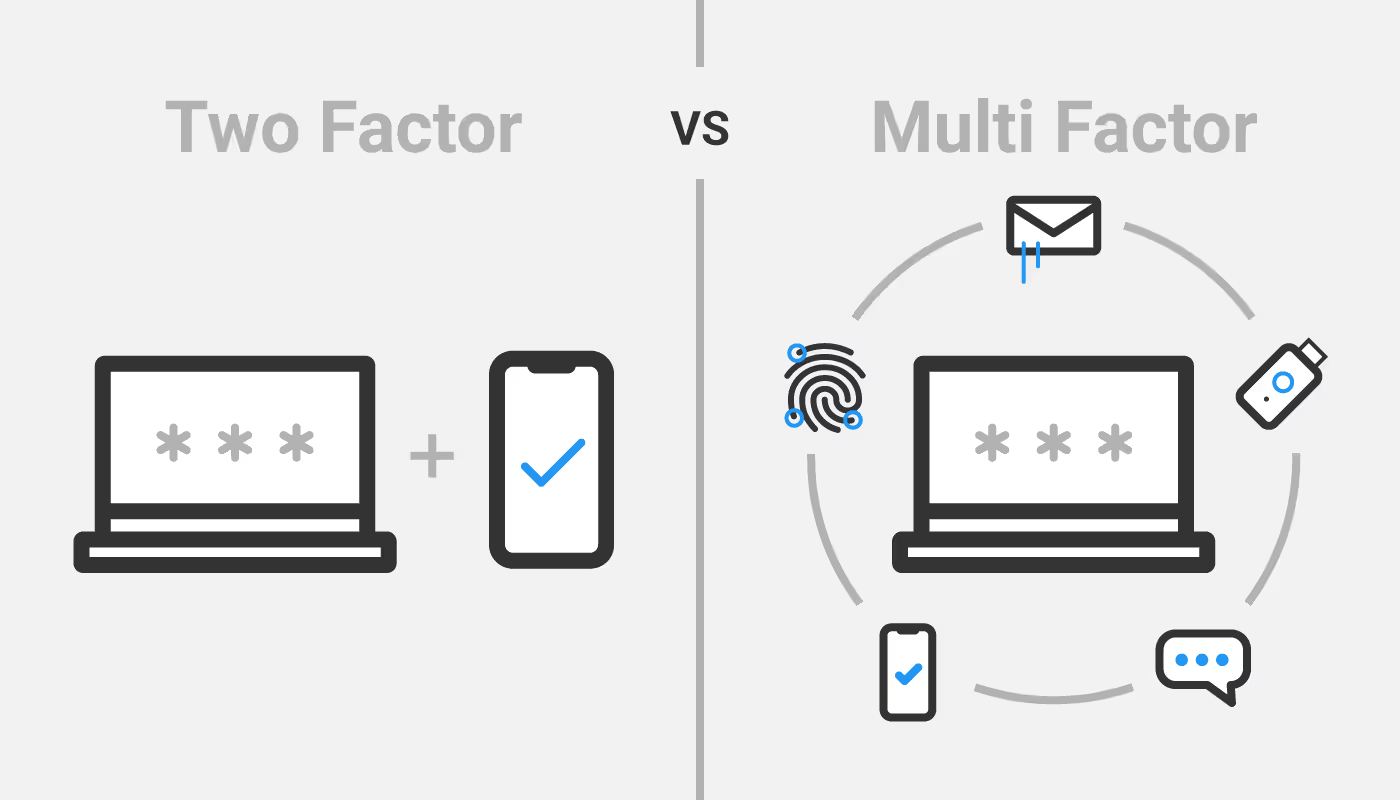
Learn how to comply with PCI DSS 4.0 Requirement 8, focusing on multi-factor authentication (MFA) and password management.

Merchants that rely on a PCI compliance program to stay compliant and protect their business often find themselves dissatisfied or frustrated by all kinds of problems including lack of support, expensive contracts, and many more.

SecurityMetrics has seen a dramatic increase in attacks specifically on ecommerce sites using iFrames to host a payment page from a 3rd party service provider.

In this case study, Anedot works with SecurityMetrics to better secure their cybersecurity infrastructure and to reach PCI DSS 4.0 compliance.

While there are various types of penetration tests like external, web application, or mobile, this blog will focus on internal tests and why they matter.

This article covers the Self-Assessment Questionnaire (SAQ) for Software-based PIN entry.

The PCI Security Standards Council (PCI SSC) recently published a limited revision to the PCI DSS in the form of v4.0.1.

External vulnerability scanning is a security practice that involves scanning and assessing the external-facing network infrastructure, systems, and applications of an organization for potential vulnerabilities.

We want to remove you from being the low-hanging fruit to hackers by improving your overall security posture. Our mission statement is to “close data security and compliance gaps to avoid a data breach.”

Endpoint security generally refers to cybersecurity tools or services that can help alert you on devices that may be compromised.
AI or artificial intelligence can be used safely by businesses that are concerned about their cybersecurity.
A number of other interesting AI cybersecurity issues are hitting our radar as customers begin taking advantage of new AI tools in their small businesses.

The most accurate way to know if you’re safe from a hacker is through live penetration testing, also called pen testing, or ethical hacking.

This blog is intended for small to medium sized-merchant businesses and attempts to answer common PCI DSS questions.
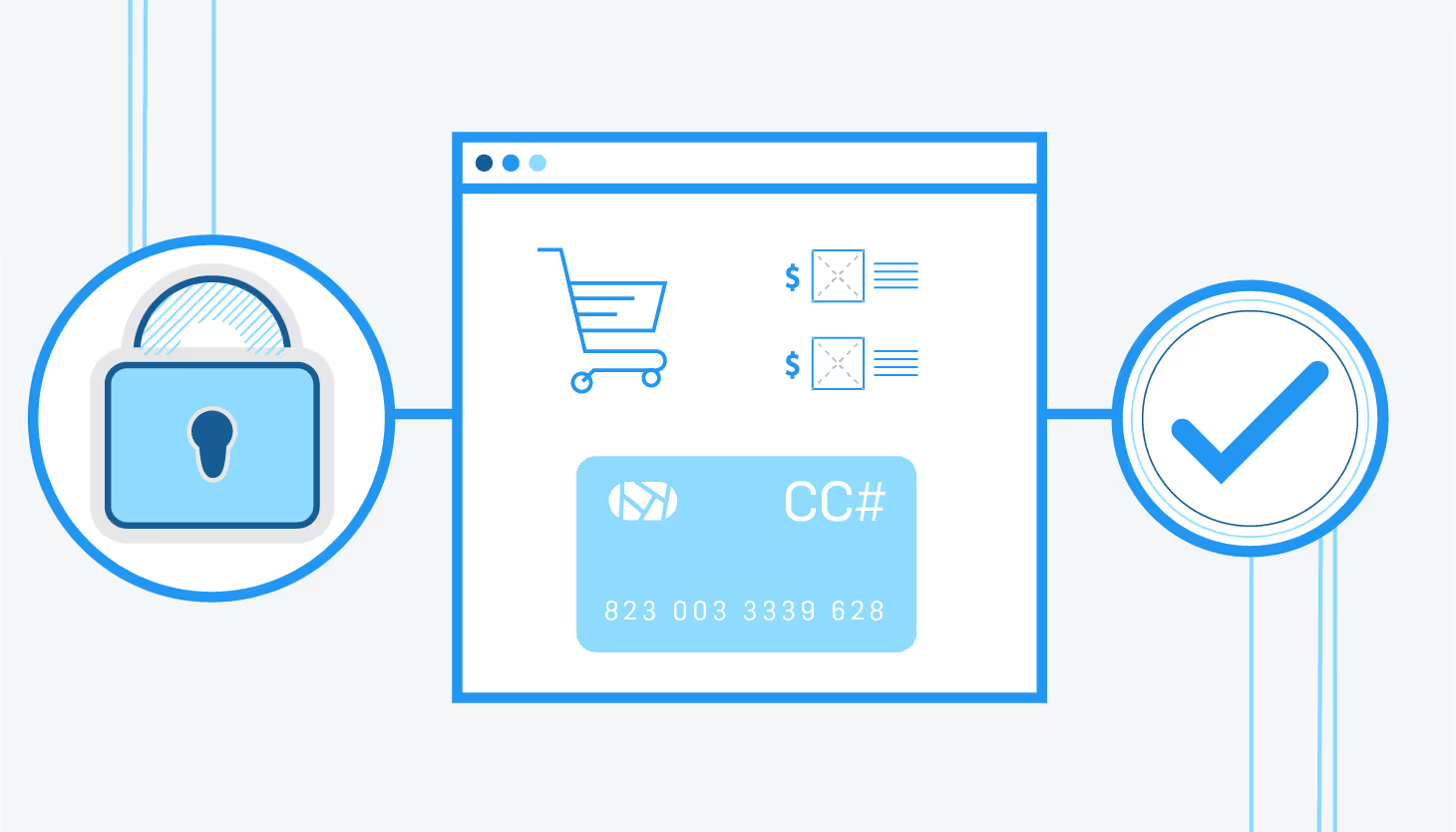
Shopping Cart Monitor has the potential to save online retailers a significant amount of money and frustration since content providers can be held liable for damages—damages that can cost retailers hundreds of millions of dollars every year.

Don't let cyber threats compromise your sensitive information. Follow these simple, cost-effective data security best practices for a secure workplace.
Like a security guard, firewalls control what goes in and what comes out.