7 Ways to Recognize a Phishing Email: Examples of Phishing Email Scams
Here are seven email phishing examples to help you recognize a malicious email and maintain email security.

Here are seven email phishing examples to help you recognize a malicious email and maintain email security.

Are you sure that email from UPS is actually from UPS? (Or Costco, Best Buy, or the myriad of unsolicited emails you receive every day?) Companies and individuals are often targeted by cybercriminals via emails designed to look like they came from a legitimate bank, government agency, or organization. In these emails, the sender asks recipients to click on a link that takes them to a page where they will confirm personal data, account information, etc.
See also: Fighting Phishing Email Scams: What You Should Know
Imagine you get an email from one of your subscription services telling you that your account has had a security breach. In the email, they tell you to reset your password by clicking the link below. While everything may seem legitimate, this, and others like it, is one of the most common scams used. This technique is what’s known as a phishing email scam.
These email phishing scams try to con you into providing your personal information or account data. Once your info is obtained, hackers create new user credentials or install malware (such as backdoors) into your system to steal sensitive data.
Phishing emails today rarely begin with, "Salutations from the son of the deposed Prince of Nigeria..." It's becoming increasingly difficult to distinguish a fake email from a verified one. However, most have subtle hints of their scammy nature. Here are seven email phishing examples to help you recognize a malicious email and maintain email security.
See also: Examples of common phishing attempts.
Spotting phishing email scams can be tricky, but the majority of them consistently have the same signs. Taking the time to look closely can make all the difference.
Requests for personal information, generic greetings or lack of greetings, misspellings, unofficial "from" email addresses, unfamiliar webpages, and misleading hyperlinks are the most common indicators of a phishing attack.
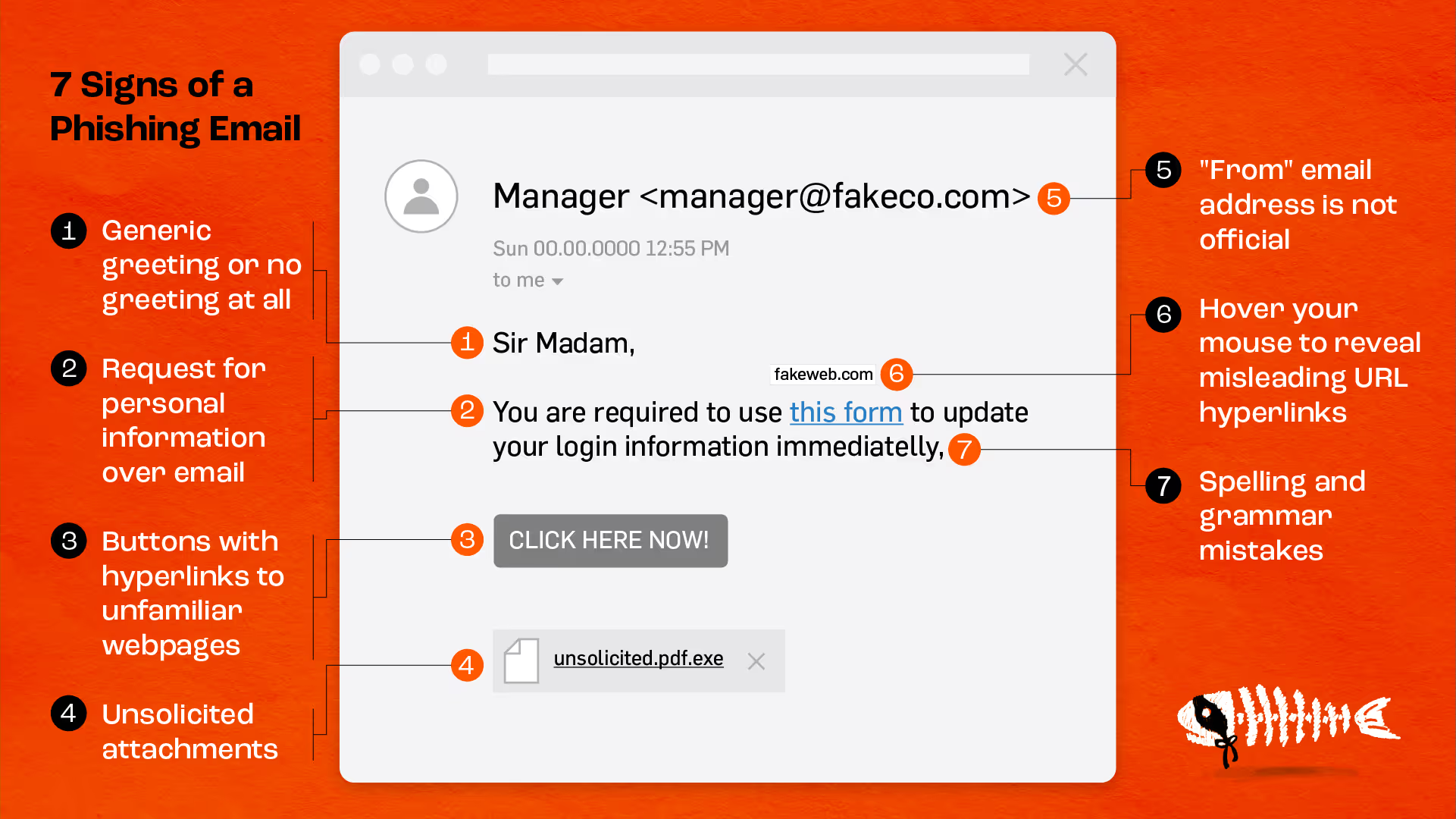
Chances are, if you receive an unsolicited email from an institution that provides a link or attachment and asks you to provide sensitive information, it’s a scam.
Most companies will not send you an email asking for passwords, credit card information, credit scores, or tax numbers, nor will they send you a link from which you need to login.
If they request any sensitive information, call the phone number listed on their official website, not the one listed in the email or message. If you didn’t ask for it, don’t respond to it.
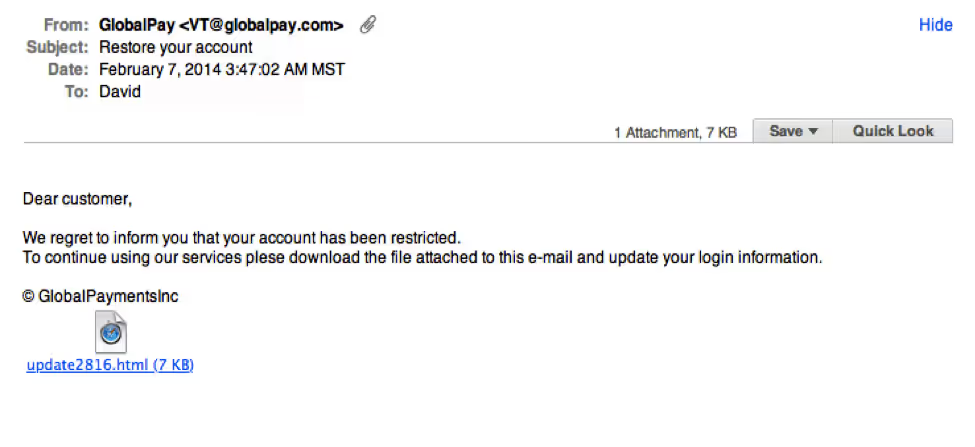
Notice the generic salutation at the beginning, and the unsolicited web link attachment?
Since scammers are typically trying to target as many people as possible, phishing emails typically use generic salutations, such as “Dear valued member,” “Dear account holder,” or “Dear customer.”
If a company you regularly receive communications from or interact with has previously required information about your account, the email would likely call you by name and direct you to contact them via phone.
BUT, some hackers simply avoid the salutation altogether. This is especially common with advertisements. The phishing email below is an excellent example. Everything in it is nearly perfect. So, how would you spot it as potentially malicious?
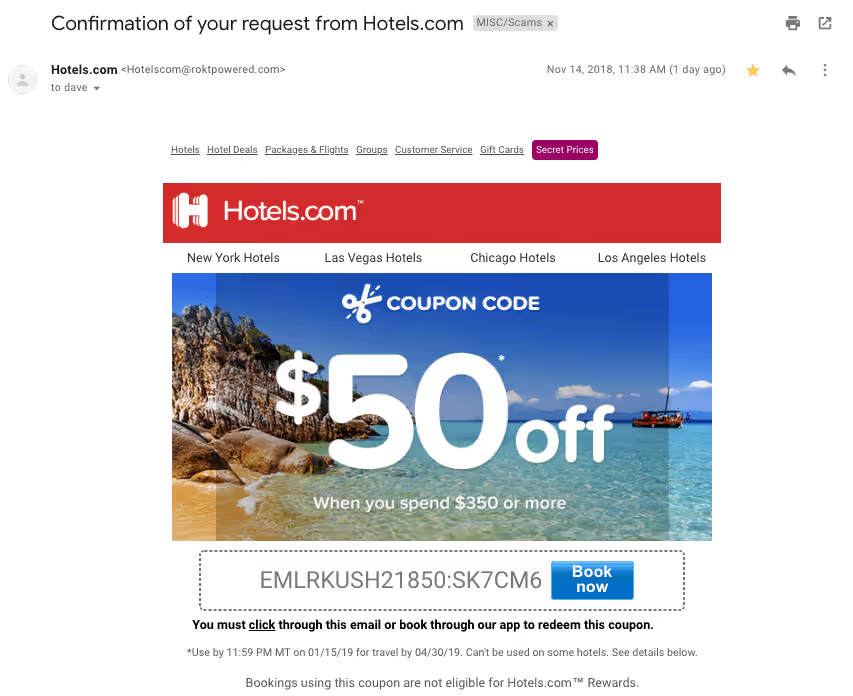
This is a very convincing email. For me, the clue was in the email domain. More on that below.
A tell-tale sign of scammers is the email address they’re sending the email from.
Don’t just check the name of the person sending you the email. Check their email address by hovering your mouse over the ‘from’ address. Make sure no alterations (like additional numbers or letters) have been made. Look at the difference between these two email addresses as an example of altered emails: "michelle@paypal.com" vs. "michelle@paypal23.com".
Just remember, this isn’t a foolproof method. Sometimes companies make use of unique or varied domains to send emails, and some smaller companies use third party email providers.
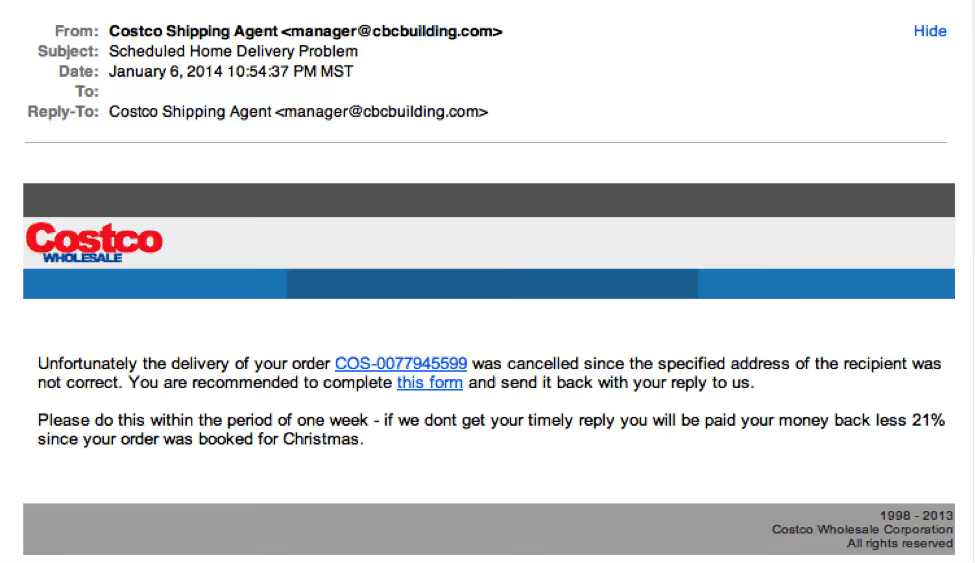
"Costco's" logo is just a bit off. This is what the Costco logo is supposed to look like.

See the difference? Subtle, no?
Possibly the easiest way to recognize a scammy email is bad grammar.
An email from a legitimate organization should be well written. Little known fact – there’s actually a purpose behind bad syntax. Hackers generally aren’t stupid. They prey on the uneducated believing them to be less observant and thus, easier targets. Take your time reading and double check any suspicious emails.
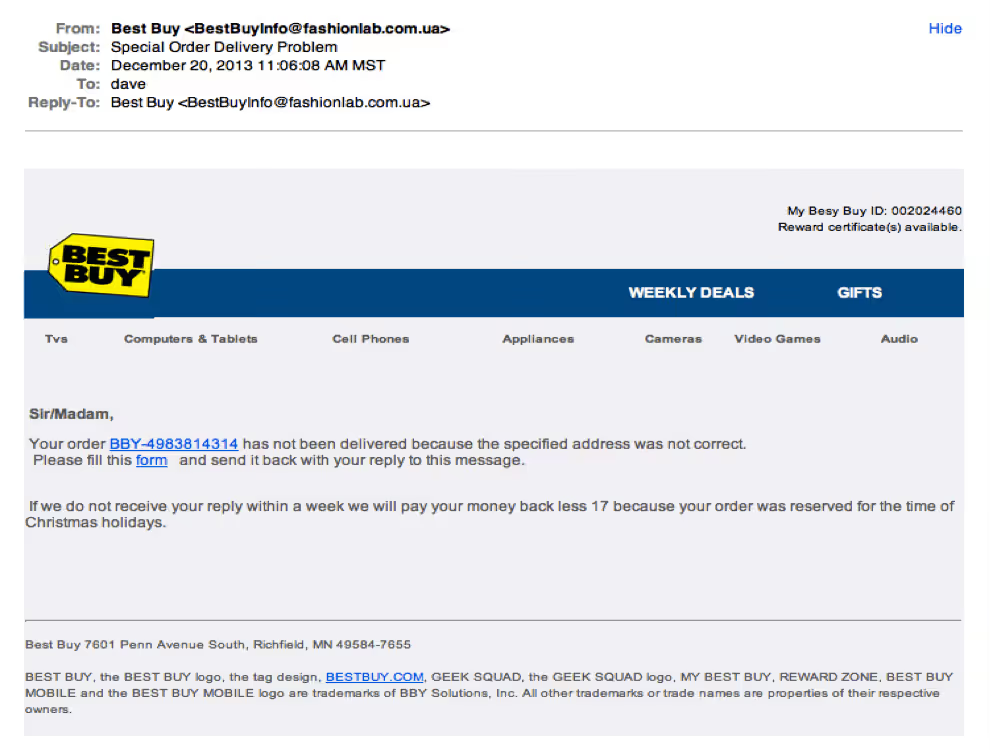
In addition to the generic salutation, grammar gaffes are usually a good clue that something is wrong. “Please fill this form…” And notice the ‘17’ reference in the middle of the sentence.
Sometimes phishing emails are coded entirely as a hyperlink. Therefore, clicking accidentally or deliberately anywhere in the email will open a fake web page, or download spam onto your computer.
If you aren’t totally sure about an email, don’t open it.
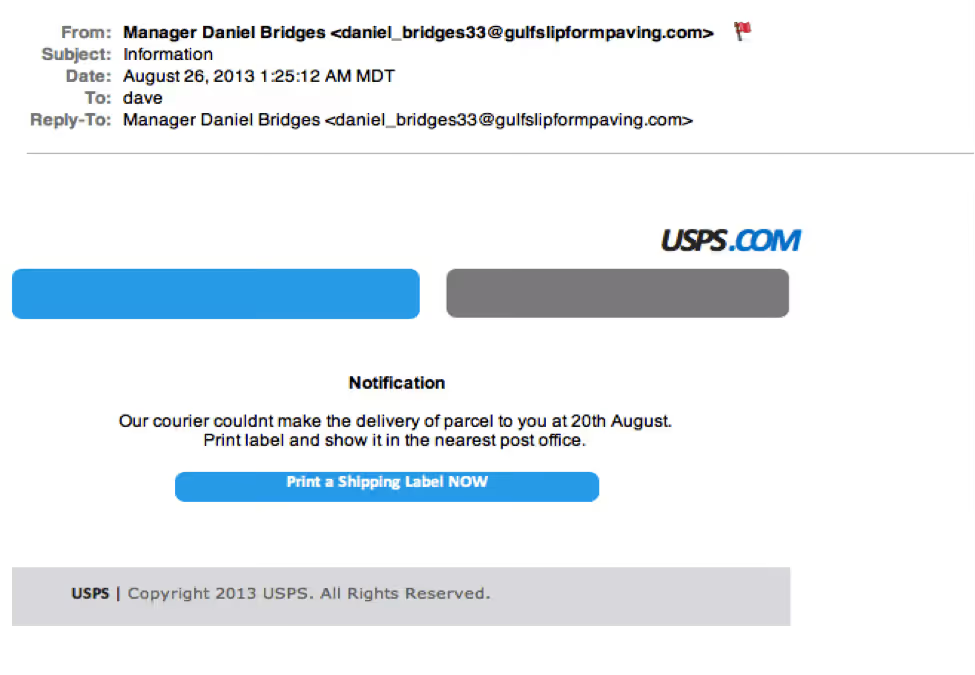
This whole email was a gigantic hyperlink, so if you clicked anywhere in the email, you would initiate the malicious attack.
Unsolicited emails that contain attachments reek of hackers. Typically, authentic institutions don’t randomly send you emails with attachments, but instead direct you to download documents or files on their own website.
Like the tips above, this method isn’t infallible. Sometimes companies that already have your email will send you information, like a white paper or billing info, that may require a download. In that case, be on the lookout for high-risk attachment file types, including .exe, .scr, and .zip.
When in doubt, contact the company directly using contact information obtained from their actual website.
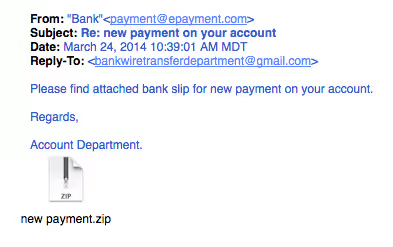
Just remember, curiosity killed the cat.
Just because a link says it’s going to send you to one place, doesn’t mean it will. Always double check URLs by hovering your mouse over the button or link you’re being asked to click.
If the link in the text isn't identical to the URL displayed as the cursor hovers over the link, that's a sure sign you will be taken to a site you don’t want to visit. If a hyperlink’s URL doesn’t seem correct, or doesn’t match the context of the email, don’t trust it.
For some additional security, when hovering your mouse over embedded links (without clicking), make sure the link begins with “https://”.
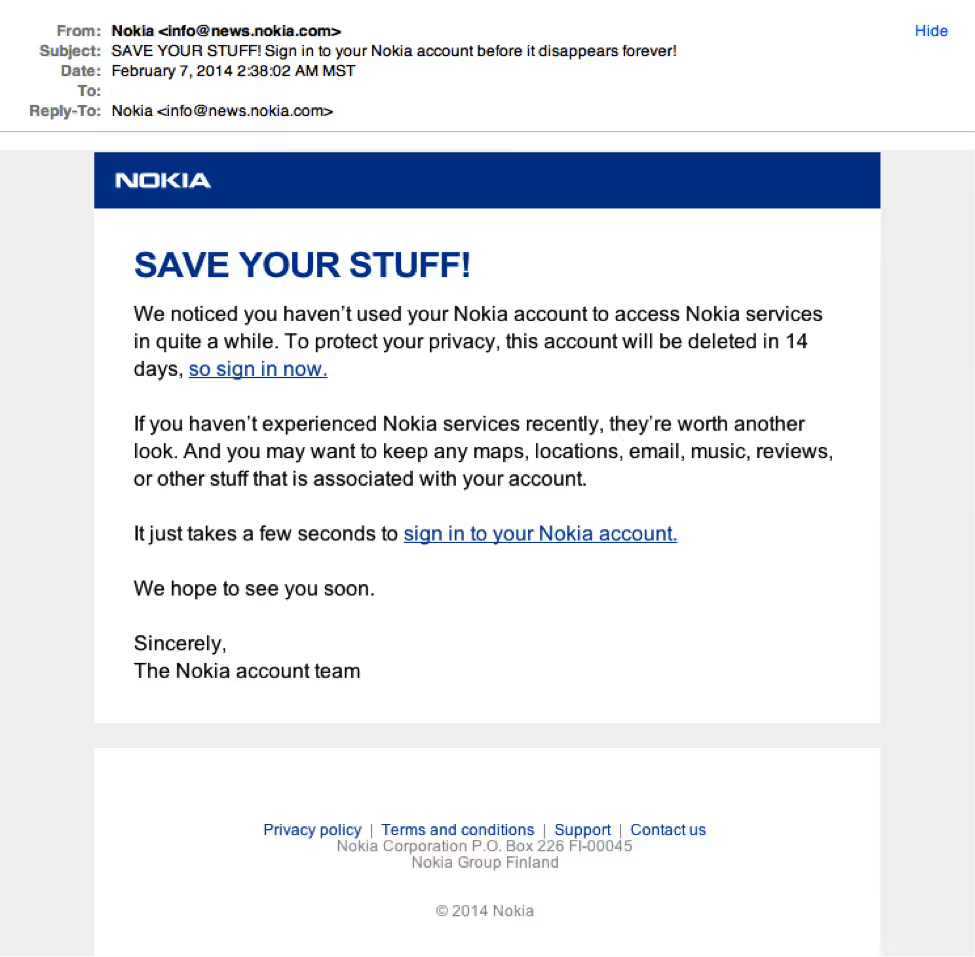
Although very convincing, the real Nokia wouldn't be sending you a "Save your stuff" email from info@news.nokia.com
Even if you have the most secure security system in the world, it only takes one untrained employee to be fooled by a phishing attack and give away the data you’ve worked so hard to protect. Make sure both you and your employees understand these specific email phishing examples and all of the telltale signs of a phishing attempt.
Phishing remains a primary method for security breaches despite decades of cybersecurity advancements. The landscape has shifted dramatically, evidenced by a reported 341% surge in malicious emails between 2023 and 2024.
This escalation is not merely a volume issue but a result of evolving tactics in which attackers use advanced tools to exploit human psychology more effectively. As these campaigns target business communications, the compromise of email accounts leads to far-reaching consequences for organizational integrity and data security.
The integration of generative artificial intelligence has fundamentally altered the quality and sophistication of phishing campaigns. Threat actors now leverage these technologies to eliminate the historic indicators of fraud, such as poor syntax, grammatical errors, and awkward phrasing. AI allows criminals to flawlessly mimic the tone, style, and branding of trusted organizations, creating highly polished communications that appear legitimate at a glance.
Furthermore, these tools facilitate the creation of convincing fake websites, enabling seamless deception that bridges the gap between the initial email and the malicious landing page.
So, distinguishing between authentic correspondence and AI-generated attacks has become increasingly challenging for even the most vigilant employees.
The lack of obvious red flags means that traditional detection methods must rely less on spotting errors and more on scrutinizing the source and context of the message. As these automated threats become more capable of bypassing standard security filters and deceiving users, organizations must prioritize advanced employee training and robust technical controls to counter the precision of modern social engineering.
Luckily, there’s some dead giveaways that an email has been AI generated. Here are my top red flags for an AI generated phishing email:
AI models are trained to produce statistically probable text, resulting in a distinct lack of human error. In a fast-paced business environment, this perfection can be a red flag.
Generative AI often follows a predictable structure: [Greeting] -> [Context/Problem] -> [Call to Action] -> [Polite Closing].
The most significant weakness of AI is its lack of real-world awareness outside of its training data or the specific prompt it was given.
Phishing is getting more and more sophisticated, especially with the new development of AI. It’s more important than ever to adequately train your employees to identify phishing emails and for them to know they shouldn’t engage. Remember, your business security might just depend on this.