Creating an incident response plan can seem overwhelming. To simplify the process, develop your incident response plan in smaller, more manageable procedures.

Complying with PCI DSS Requirement 8 deals with user accounts, passwords, and password management. This requirement is all about having unique, difficult-to-discover account information.

This blog answers common questions about HITRUST Assessments and why a HITRUST assessment might be a good choice for your organization.

Each year, SecurityMetrics releases a blog post featuring our major cybersecurity predictions, featuring insights from our veteran team of cybersecurity, audit, and compliance staff.

Read this blog to discover what SecurityMetrics forensic analysts got right and wrong about 2024 cybersecurity breaches and what we can learn from this past year.

Recently two requirements that were part of SAQ A were removed, namely PCI DSS 6.4.3 and 11.6.1.

Security Academy is a beginner-level, free course that you can return to if you have cybersecurity questions.

Find out about the latest about PCI DSS v4.0.1 requirement 6.4.2, which mandates that ecommerce merchants implement a Web Application Firewall (WAF) or equivalent security measures to protect their online payment environments.

This year’s HIPAA guide includes an easy-to-understand introduction that covers how to read the guide, an executive summary, and an overview of this year’s new trends and stats.

Read this blog to learn how 2024 compared to 2023 regarding HIPAA Security, Breach Notification, and Privacy Rules trends.

The PCI Council just announced a big change for merchants that use SAQ A, regarding specific PCI requirements.

Complying with the 12 requirements of PCI can be complicated for those who must meet PCI compliance. Read this blog to get an in-depth description of each requirement, tips for achieving requirements, and answers to frequently asked PCI questions.

Discover the most important resources of 2024 so you don’t miss out.

HITRUST is becoming increasingly required by organizations to ensure robust protection of sensitive data. Manage third-party risk effectively.
Discover the answers you need as an acquirer to navigate new PCI updates, PCI program questions, and merchant concerns.

The main purpose of a penetration test is to stay one step ahead of the bad guys by finding your weaknesses with the help of experts exploring your mobile app and supporting systems.

Understanding the role of an ISO in the payment process can be tricky. This blog outlines the most frequently asked questions surrounding ISOs and their pros and cons.

This blog post is for anybody who's interested in external pen testing basics, the types of things found when pen testing, and the process that you go through when completing them.

This blog explores the main ideas from the webinar “How to Protect Your Ecommerce Website Against Eskimming,” and the latest threats attacking the e-commerce space.

When it comes to your business, choosing the right, knowledgeable partner can make all the difference in preventing audit fatigue.
There’s no need to put up with a PCI program that isn’t meeting your expectations.

This blog is a summary and compendium to the SecurityMetrics’ Webinar “How to Protect Your Ecommerce Website Against Skimming”, hosted by Matt Heffelfinger and Aaron Willis.
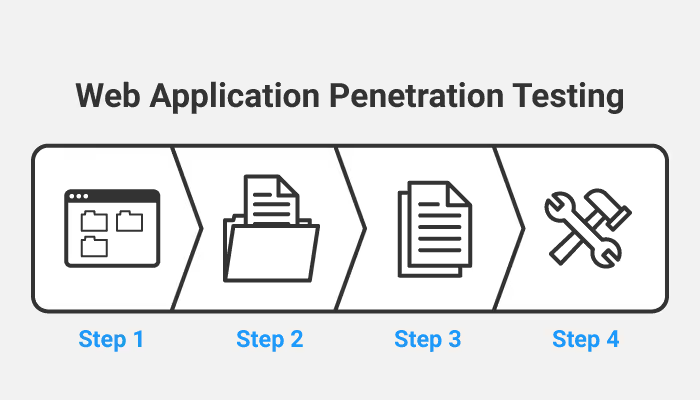
Read this blog to understand the methodology, scope, and best practices for conducting effective web application penetration testing.