Phishing Types, Tactics, and Techniques
To effectively protect your business, it's crucial to understand the various types of phishing tactics and how to prevent them.

To effectively protect your business, it's crucial to understand the various types of phishing tactics and how to prevent them.

Phishing has evolved into a multifaceted challenge, encompassing a variety of tactics and techniques that extend beyond the classic email-based scams. While phishing is a widely recognized form of social engineering and may seem trite compared to other threats, phishing remains one of the biggest security weaknesses to organizations.
To effectively protect your business, it's crucial to understand the various types of social engineering attacks and how to prevent them.
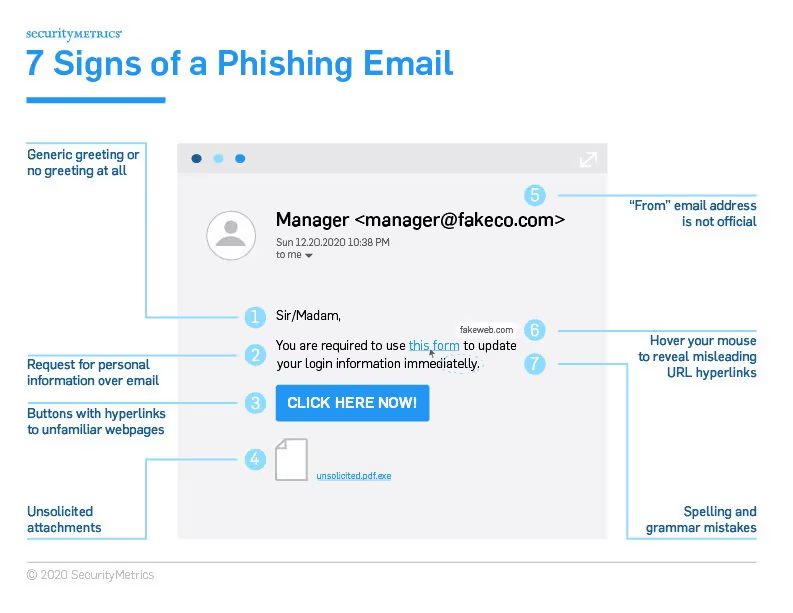
See also: 7 Ways to Recognize a Phishing Email: Email Phishing Examples
Overview: Angler phishing is a phishing tactic that uses fake customer service accounts. It relies on spoofed email addresses and malicious links to deceive employees into divulging login credentials, credit card details, employee information, or other personal data.
Risk Level: Medium to High
Preventive Measures: Employees interacting with customer data, such as sales and marketing teams, should be particularly vigilant. Common lures include emails about expiring login information, password resets, subscription renewals, fake receipts, and customer service requests.
Overview: Spear phishing is a targeted form of phishing where specific individuals within an organization are chosen as victims. Threat actors conduct research to craft highly convincing emails or messages, often posing as trusted contacts.
Risk Level: High to Very High
Preventive Measures: While any employee with an email account can be a target, those dealing with customer data, PCI data, PII data, intellectual property, or personal information should maintain a heightened state of awareness.
Overview: Whaling focuses on high-level executives, managers, supervisors, and business owners. Threat actors invest time in researching and often spoof email addresses or messages to create a sense of urgency.
Risk Level: High to Extremely High
Preventive Measures: Executives and leaders should exercise heightened awareness. Employees should verify unusual requests and confirm their authenticity with managers or supervisors.
Overview: Baiting relies on employees' goodwill. Threat actors offer enticing bait, such as free gift cards in exchange for completing surveys, to trick employees into disclosing sensitive information.
Risk Level: Medium to High
Preventive Measures: Employees should be cautious of offers that seem too good to be true, especially if they involve providing personal information.
Overview: Honey trap attacks exploit romantic or emotional connections to manipulate employees into providing confidential information or assisting in various ways. Threat actors build trust over time. The “Nigerian Prince” email is a classic example of this scam, but this type of phishing attack continues to evolve with new technology across additional social platforms.
Risk Level: Low to Medium
Preventive Measures: Employees should be educated about recognizing warning signs and be offered HR-led support systems to resist manipulation.
Overview: Pretexting is a sophisticated form of phishing that involves threat actors posing as legitimate entities, such as vendors, contractors, or government agencies. They create a false sense of urgency to solicit information.
Risk Level: Medium to High
Preventive Measures: Employees should be cautious when dealing with urgent requests, even from seemingly legitimate sources. Verification and authentication processes are essential.
Overview: SMS phishing, or smishing, targets individuals through text messages impersonating trusted sources. Cybercriminals often pretend to be CEOs or business owners.
Risk Level: High to Very High
Preventive Measures: Awareness and caution are critical, especially in organizations that rely heavily on cell phones for communication. Employees should verify unusual requests, and multi-factor authentication should be enforced.
Overview: Vishing is a social engineering technique that uses phone calls to trick individuals into divulging sensitive information or performing actions that compromise their security. Perpetrators often impersonate trustworthy entities, such as banks, government agencies, or tech support, to extract personal data or access protected systems. This is becoming a more popular tactic as AI technology evolves.
Risk Level: Medium to High
Preventive Measures: Implementing employee training and awareness programs to recognize vishing attempts is crucial. Encourage skepticism towards unsolicited calls requesting sensitive information. Verification of the caller's identity through known contact details or official channels can prevent falling victim to vishing attacks. Establish and uphold robust verification processes before sharing any confidential information over the phone.
Overview: Watering hole attacks compromise legitimate websites. When users log in, their credentials are captured and used to breach the network. Attackers move laterally, looking for valuable data.
Risk Level: Medium to High
Preventive Measures: Multi-factor authentication, strong passwords, and regular password changes are essential. Expired employee accounts should be promptly removed.
Regular training, awareness programs, and the implementation of security measures, such as multi-factor authentication, can significantly reduce the risk of falling victim to phishing attacks. Remember, a well-informed and cautious team is your organization's first line of defense against these evolving cyber threats.
To build a robust defense, you and your employees must:
Phishing attacks are relentless and ever-changing, but with a well-informed and cautious team, you can significantly reduce your organization's vulnerability. Remember that your employees are your first line of defense against these evolving cyber threats.
By combining ongoing education and a cooperative work culture, you can build a resilient defense that safeguards your business against modern phishing threats.