
While most healthcare entities follow the Privacy Rule fairly well, many aren’t compliant in the HIPAA Security Rule.

In 2020, we hosted the first annual SecurityMetrics Summit; a virtual data security and compliance conference on September 23rd and 24th.

Learn how to maximize security through simple practices and employee training.
VPNs are a popular tool that helps businesses make sure outside users are authorized and that transmitted data is encrypted.

The year 2020 was surprising in many ways and the digital forensics industry offered some surprises as well as some more predictable outcomes.

With ecommerce attacks on the rise, it's crucial for businesses to learn how to strengthen their ecommerce security.

Merchants using the SAQ C to validate their PCI DSS compliance should be aware of changes that were introduced into this questionnaire during the publication of the SAQ C version 4.0.

Learn the three essential steps to help you effectively prepare for a HIPAA audit.
Learn 5 basic practices to get PCI compliant, even if you're new to PCI or a compliance veteran.

Web application firewalls rest in front of public-facing web applications to monitor, detect, and prevent web-based attacks.
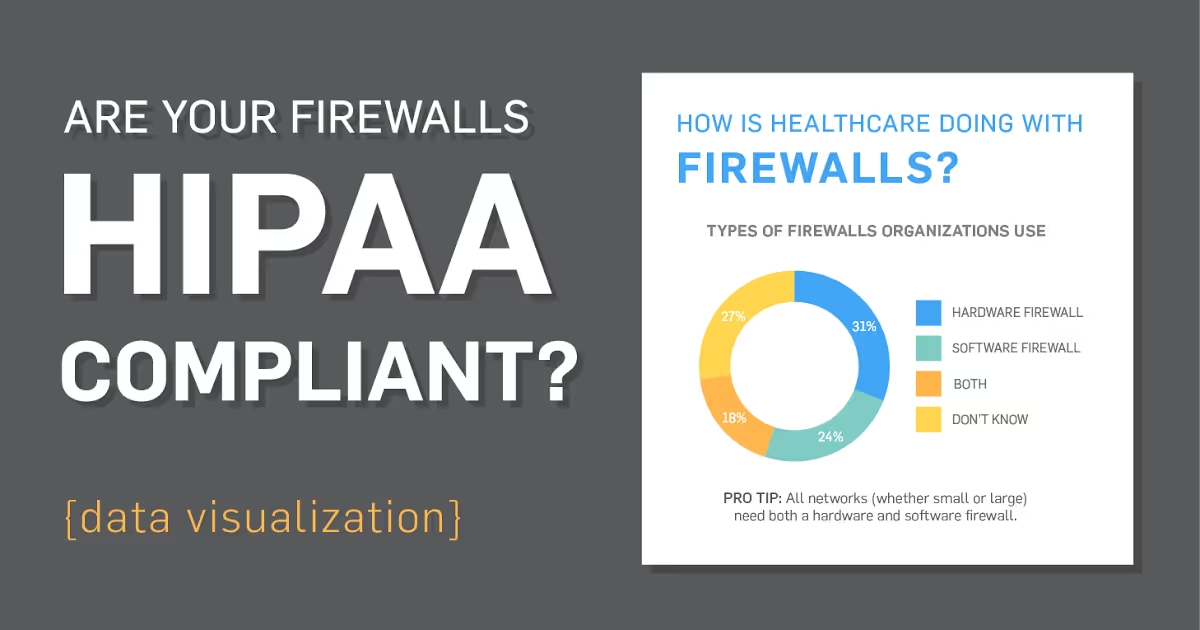
See how healthcare organizations are managing their firewalls.
PCI Requirement 1 deals with setting up and configuring firewalls to protect your business data.

PCI DSS requires anti-malware software to be installed on all systems that are commonly affected by malware (e.g., Windows).

With March 31, 2025 as a target destination, managed security service providers and enterprises from across the digital commerce chain are taking a measured approach to implementing PCI DSS version 4.0.

This blog will discuss changes to the PCI DSS 4.0 SAQ questionnaires and is based on our Webinar "PCI DSS 4.0: What's New and How It Affects You."

This blog will discuss changes made to the SAQ P2PE version 4.0 and will review the process of performing a self-assessment using the SAQ P2PE.

Here are some questions participants asked in our webinar, “PCI DSS 4.0: What Is New and How It Affects You.”

While the PCI v4 standard is not expected to be finalized and released until the end of 2020 or the beginning of 2021, the PCI Security Standards Council has made some information available to the general public on what some of the changes might be.

By following basic security practices and policies, you can make your devices HIPAA compliant and keep your data safe.

Here are 5 Blogs to Help You Survive PCI DSS and Prevent Security Breaches This Year. We cover formjacking, penetration tests, PCI DSS checklists, PCI DSS audits, as well as preparing for incident response.

Every covered entity that uses business associates is required to obtain assurances that their business associates treat patient data the way you and HHS require them to.

System administrators have the responsibility to ensure all system components (e.g., servers, firewalls, routers, workstations) and software are updated with critical security patches within 30 days of when they are released to the public.