
Let’s take a look at some of the different costs your business could incur as a result of a data breach.

GDPR applies to any organization that processes or holds the personal data of persons residing in the European Union. PCI applies to organizations that handle credit cards from the major card brands.

If you've experienced a data breach, you will probably need a forensic investigation to determine the cause of the breach. Here are some forensic faqs to help you understand the process of a forensic investigation.

A PCI program is a system that acquirers use to keep track of their merchants PCI compliance, and for merchants to receive the training and tools they need to achieve PCI compliance and remain PCI compliant.

Simply installing a firewall on your organization’s network perimeter doesn’t secure your network or make you HIPAA compliant. Proper configuration is critical for HIPAA compliant firewalls.
What should you look for in a PCI program and how will you know which PCI program is right for you?

How do you secure data on mobile devices? Physical security and mobile device policies are good at protecting the device itself, but another way to protect the data on the device is mobile encryption.

To discover your PCI scope and what must be included for yourPCI compliance, you need to identify anything that processes, stores, or transmits cardholder data, and then evaluate what people and systems are communicating with your systems.

Specific HITRUST requirements are available through HITRUST’s MyCSF portal and will include various implementations of foundational security measures and controls depending on your organization and the type of HITRUST assessment you are performing.

An example of insecure credit card number storage comes from one of our PCI assessors, where a company explained how they processed their credit cards.

Overview of key changes in the CIS controls update. See what’s new in the CIS Controls (v8) and how this free resource can help maximize your security.
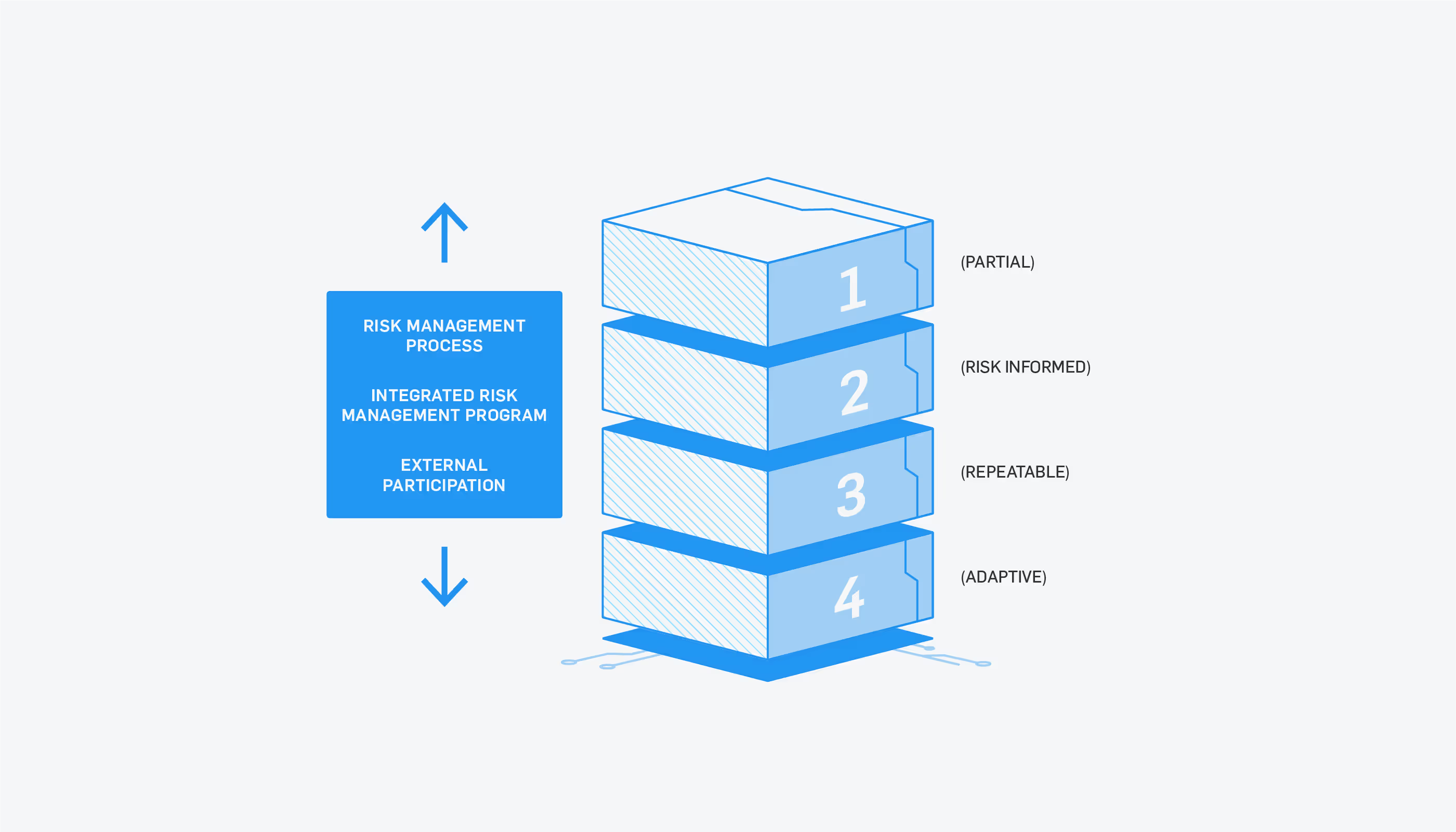
The NIST cybersecurity framework can help guide small-to-medium sized organizations improve their cybersecurity posture.

Criminals have countless methods and types of phishing emails to trick email users.

How do you block access to your systems (and sensitive data) from hackers in the outside world?

System logs are part of HIPAA compliance and specifically mentioned in two different requirements.
Log management and regular log review could help identify malicious attacks on your system.

Merchants must “address all known security vulnerabilities and [be] consistent with industry-accepted system hardening standards.”

Learn how to help your employees be better prepared to fight against social engineering tactics.
If you’re a service provider, you may have some different PCI requirements based on what level you are.

The biggest difference between SAQ A and SAQ A-EP is based on how cardholder data is handled.

There are some key changes to the PCI DSS 4.0 SAQ questionnaires you will want to be aware of.
You will need to be compliant with PCI DSS 4.0 by March 31, 2025. We recommend starting your transition to 4.0 by reading the documents that explain the new PCI standard, including the executive summary, which has a lot of good information in it.