Two Factor Authentication – Security Beyond Passwords
Is two-factor authentication perfect? No, but it does make a hacker’s job more difficult.
Is two-factor authentication perfect? No, but it does make a hacker’s job more difficult.

Passwords alone have been shown to provide poor protection to our sensitive data, especially over the past few years. Many reasons contribute to this, but the biggest is probably the attacker’s growing ability to test and retest different passwords over and over until succeeding. This is known as brute-force password cracking.
According to Fast Company, brute-force password-hacking methods can churn through billions to hundreds of billions of passwords per second.
August 2014 revealed that Russian hackers stole 1.2 billion passwords. In September 2014, 5 million usernames and passwords were leaked on a Russian Bitcoin forum. In February 2015, 10 million passwords were released by a security researcher to show how easy it is to gain access to stolen credentials. How many of you use the same password for multiple accounts?
So…if hackers have a giant online bank of passwords, how are we supposed to keep our information safe through username and password authentication? Luckily the technology to assist us already exists. It’s called two factor authentication.
See also: SecurityMetrics PCI Guide
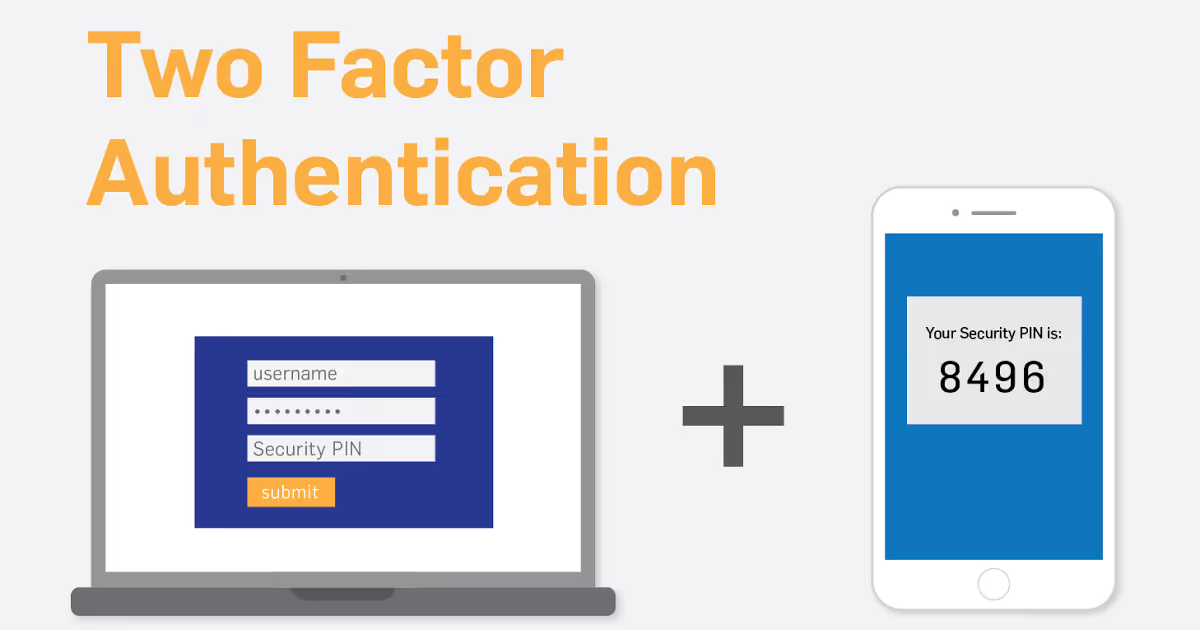
Two factor authentication, also abbreviated as TFA or 2fa, is an extra layer of security during the authentication process. Two independent methods of authentication are required to access an application, network, or computer. This ensures you (and only you) gets access to sensitive information.
Without two factor authentication, you are required only to enter a username and password. The password is the only factor of authentication, and as we know, passwords are just waiting to be hacked.
To qualify, 2fa must contain two of the following factors:
Here are three real-world applications:
Learn how to enable two-factor authentication online.
There are a lot of problems people run into when configuring two-factor authentication.
Here are the top three myths I see when helping people configure multi factor authentication at their business.

FALSE! More of the same factor does not automatically create two factor authentication, or extra security. You can’t use two passwords as your two factors. You can’t use a password and a security question as your two factors. You can’t use two SMS text codes as your two factors. You must configure two different factors of authentication (see list of possible factors above) to qualify as two factor authentication.
FALSE! Multi factor authentication improves security in a huge way, but it doesn’t make your business invincible. For example: Say you use a password and SMS text as your two factors. What if a hacker steals your phone and knows your password? What if your factor relies on a third party security? Remember when RSA tokens were breached in 2011? Security is never perfect.
FALSE! Yes, two-factor authentication makes it a bit more inconvenient to login, and it’s not impenetrable. But…it also bumps up the security. It’s also important to note that two-factor authentication is a PCI DSS requirement. (Requirement 8.3) If you use a two-factor authentication, a hacker has to obtain two forms of authentication, instead of just your password. Data is useless to an attacker without the second factor.
Not all your online accounts, hardware, and software will have the ability to be configured for two-factor authentication, but many do. The following is a list of applications that (if possible) should be configured with two-factor authentication where possible:
Some sites that use two-factor will also alert you via email or text message if someone tries to log into your account using a device they don’t recognize, or when an incorrect password is entered.
Here’s a list of sites that support two factor authentication.
See also: INFOGRAPHIC: Cybercriminals Love When You Use Remote Access
Is two-factor authentication perfect? No, but it does make a hacker’s job more difficult. It is a necessary layer of protection for your data.
In the future, multi factor authentication will make single-factor passwords obsolete. In addition, many more second factor options will be available for authentication, such as vein scanners and microchip implants.
Perhaps attackers will become so advanced in the future that three-factor authentication will be the new norm. But for now, two steps is a small effort businesses can and should take for greater security.