How to Choose a Safe and Secure VPN
VPNs are a popular tool that helps businesses make sure outside users are authorized and that transmitted data is encrypted.
VPNs are a popular tool that helps businesses make sure outside users are authorized and that transmitted data is encrypted.

As companies shift to incorporate more remote work, payment data security often comes into question. Employees are accessing enterprise data from a variety of environments. Companies need to understand how to implement tools and technology in these environments in a secure way that will protect data from threat actors. VPNs are a popular tool that can help businesses make sure outside users are authorized and that transmitted data is encrypted. This blog will explore the security considerations and threat trends associated with using a VPN and will help readers know what to look out for when choosing a VPN provider.
Threat actors are hammering virtual private network (VPN) providers with attack after attack. In the first week of March 2021 alone, hackers stole the data of over 21 million mobile VPN app users and sold it online. And in July of last year, seven VPN services leaked the data of over 20 million users.
Horror stories like these riddle cybersecurity headlines and call the security of the entire VPN ecosystem into question. So-called “free” VPNs pose an enormous risk to users, and security researchers recently revealed that over 105 million users of free VPN apps in the Google Play Store could potentially be compromised. Many of these apps have been removed from the Google Play Store, but unfortunately, VPN breaches continue to escalate. As of now, there are nearly 500 known VPN vulnerabilities registered in the CVE database.
So, how secure are VPN providers? And how do you know what signs to look for when many providers are breaking the promises made in their privacy policies? This blog article will explore this issue as well as help you understand “no-log” or “zero-log” VPNs.
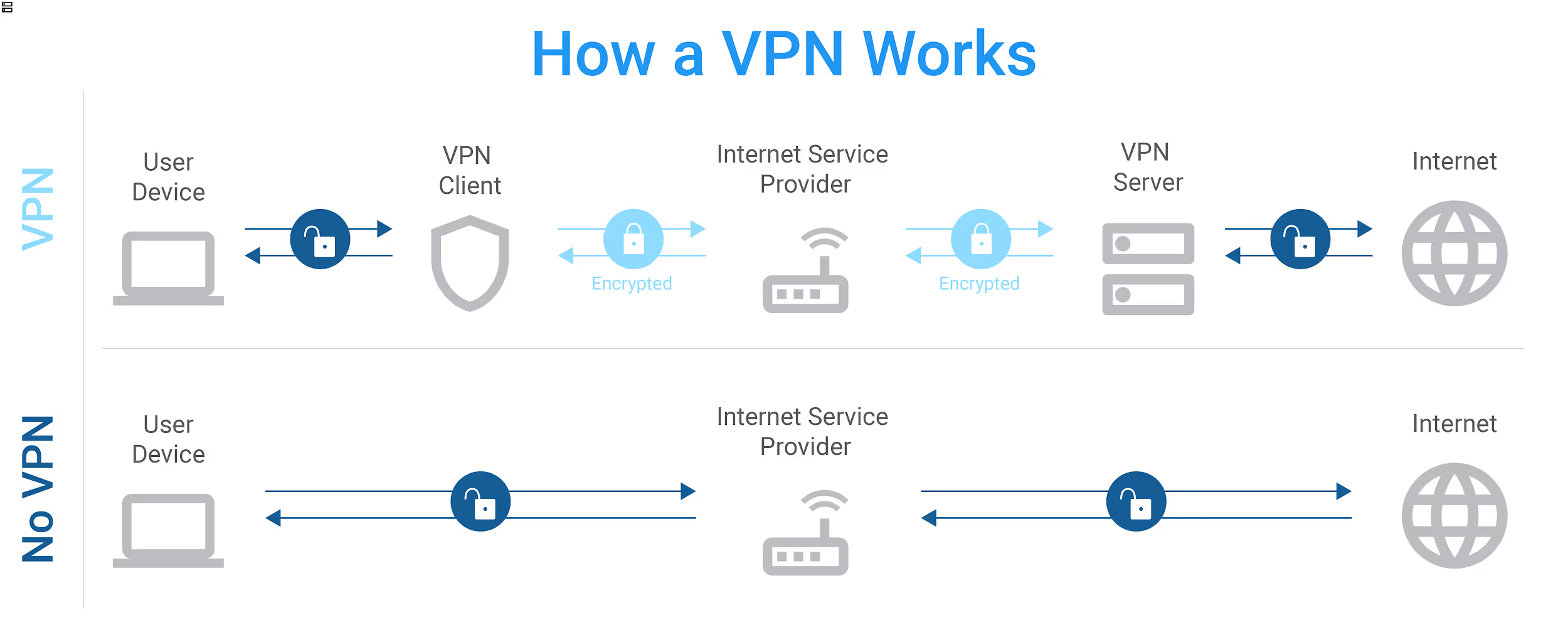
When you install and use a VPN, it acts as an intermediary, rerouting your Internet data traffic onto a private server and through an encrypted, secure pipeline to and from your destination. Your data traffic will appear to come from the server, not your device’s IP address.
You can purchase a VPN directly from a VPN provider website, or through the Apple App Store or Google Play Store.
Due to the COVID pandemic, VPNs have exploded in popularity. They are a great tool to help employees work remotely or connect to a country outside of their geographic region. For companies that want to provide their employees with privacy, anonymity, and security, VPNs can help employees create a secure connection across public networks.
VPNs can be used in a variety of situations. For example, when companies want the confidence that their data is encrypted from end to end or when users work from public places like hotels, coffee shops, or in their cars and want to ensure their location is private and their connection is secure. Some people install VPNs at home so they can watch TV shows or sporting events that are restricted in their country.
Today, global VPN usage has increased to unprecedented levels. Between March 8 and 22, 2020, VPN provider Atlas reported a 124% surge. Threat actors have taken notice and are gravitating toward VPN-related attack opportunities.
The 2021 VPN Risk Report reveals the current state of VPNs; their vulnerabilities, risks, and the entire remote access environment. The report highlights some pretty remarkable stats, with 93% of companies reporting that they leverage VPN services in their environment, and 94% of all those surveyed indicating they are aware cybercriminals are targeting VPNs.
In short, threat actors know that with the global shift to remote work, businesses and individuals are using VPNs more than ever.
No; avoid free VPNs. Free VPNs shouldn’t be considered for use to protect your business or users. They are very tempting because they are free; however, you must be aware that at some point the VPN–or any mobile app–is collecting user data to be sold to third parties. Oftentimes, the app is free because expenses are paid by third-party advertisers.
Remember that you want security for your data and trust in your company–they are valuable to you, and they do come with a cost. Use these tips to confidently research and choose a VPN service for your business.
To learn more about protecting your business locations from cyberattacks, visit this website.