PCI 4.0 Summary of Changes
PCI 4.0 summary of changes including new requirements that have been added to the standard.

PCI 4.0 summary of changes including new requirements that have been added to the standard.

*This article was taken from our PCI Guide. For more information on this topic, download our free PCI Guide.
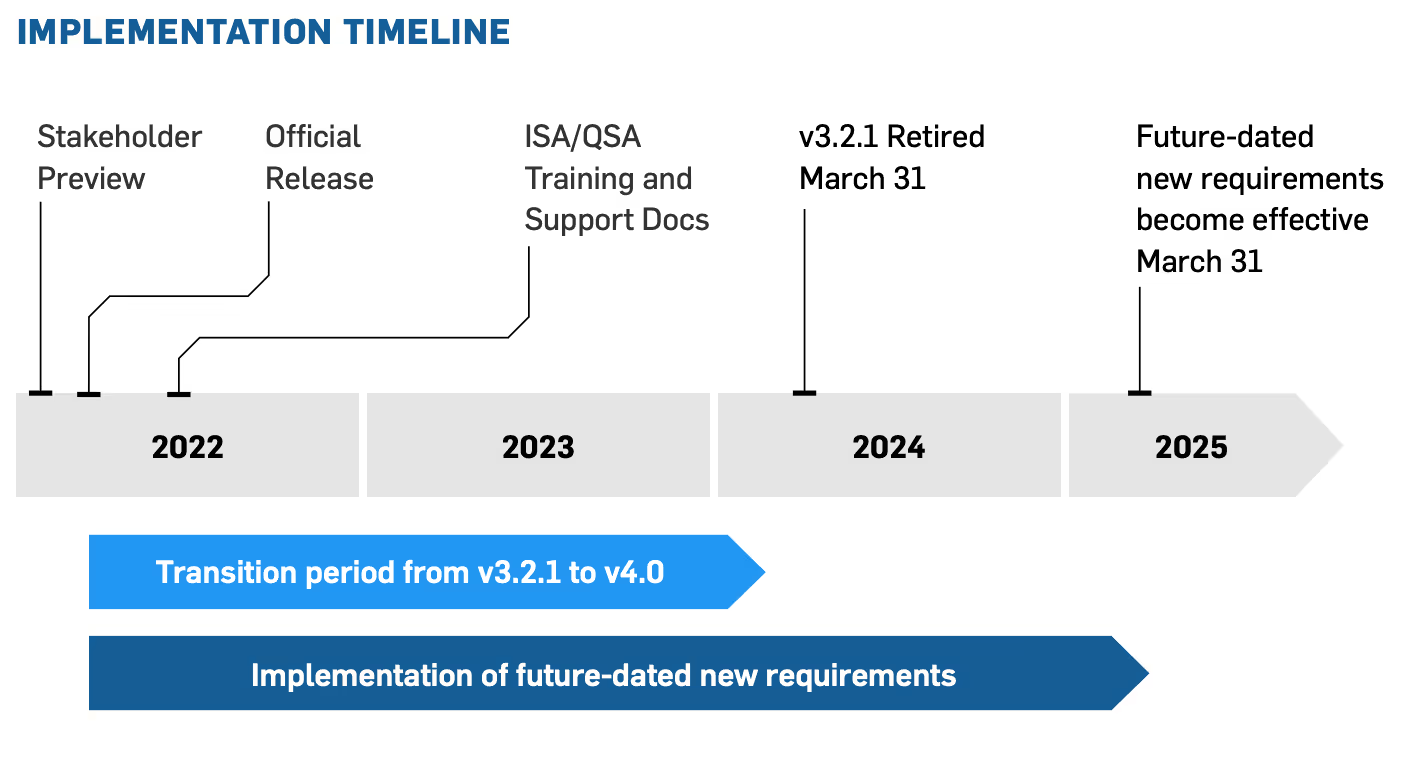
The adoption of PCI DSS version 4.0 includes an overlapping sunset date for PCI DSS version 3.2.1 so that the transition between versions will be smooth.
The adjacent diagram shows the PCI DSS 4.0 transition timeline based on information by the PCI Council. One thing to focus on is that ample time has been provided for the transition from PCI DSS 3.2.1 to PCI DSS 4.0.
In addition, many new requirements being added to the standard are future-dated to allow new processes to be developed before any new requirements will be enforced. We have included this section to give you a quick introduction to PCI DSS 4.0 and some of the larger changes.
Why did the PCI Council make a major rewrite of the PCI DSS when it is considered to be a fairly mature standard?
There are four major reasons for the changes:
As time moves on, technology changes and so do the attack vectors of bad actors trying to compromise systems.
It is important to keep up with this changing technology. PCI DSS 4.0 addresses these changes, from scoping to cloud computing. The following table shows some of the areas of further guidance and definition. This is not an exhaustive list but will give you some ideas of what has changed.
The following information details the areas of PCI DSS 4.0 evolution:

From the beginning, PCI DSS requirements were created to help organizations develop security best practice habits that would be followed year-round, rather than only during an annual assessment period.
Many organizations have been able to make this transition to the mindset of security as a lifestyle, while others are still focused on passing an assessment and moving on.
For example, there were changes to include more gathering of validation information over a period of time to support and ensure that a continuous security process is in place.
The PCI Council has looked at validation methods and procedures to make sure they are meshing with the new PCI DSS 4.0 release. The SAQ and AOC processes and contents have been evaluated, enhanced, and released in April 2022.
The new customized approach methods are not supported in current SAQ validation methods.
QSAs sometimes get asked the question, “our methods are secure; can’t I meet this requirement another way?” The response had to be “We could look at defining a compensating control, but that is considered a temporary solution until you can meet the requirement the right way.”
Version 4.0 of the PCI standard will try to resolve this scenario by introducing the concept of validation of a security control using a customized approach. Companies that adequately meet requirements with existing controls can continue to use these controls as a viable way to achieve compliance.
Past validation methodologies will now be known as a Defined Approach. This is essentially what we have been doing for the past 17 years. Either approach option can be used for a PCI DSS requirement and approaches can even be mixed up within a single Report on Compliance (RoC).
PCI DSS 4.0 introduces the concept that not all security approaches are the same and that there may be many ways to achieve a security objective. Version 4.0 will allow customization of requirements and testing procedures in order to accommodate this.
Many companies have security solutions in place that may meet the intent of a security objective but not meet a specific requirement. This approach could let entities show how their specific solution meets the intent of the security objective and addresses the risk, and therefore provides an alternative way to meet the requirement. This new approach will take the place of compensating controls in the PCI DSS 4.0 standard.
The PCI council has stated that “Unlike compensating controls, customized validation will not require a business or technical justification for meeting the requirements using alternative methods, as the requirements will now be outcome-based.”
While this new validation method may sound simple, it will most likely result in more assessment work initially for the entity in order to prepare documentation and risk assessment data for a QSA to evaluate. It will then require specialized testing procedures to be developed by the QSA and agreed upon by the entity.
The customized approach will not be for everyone and will be most suited for entities with mature security and risk assessment processes in place.
The custom process provides the advantage of defining a more permanent solution for compliance validation of specialized security controls. This is different from previous temporary compensating controls in earlier versions of the standard, where you had to document a justification for the control with a business or technical constraint.
The customized approach offers more validation flexibility, but it’s not ideal for everyone. The following figure illustrates where responsibilities lie when using the customized approach:

Relying on a security implementation you already have in place may save on new capital expenses, but it will require more work on your part. You will need to thoroughly document, test, and conduct risk analysis efforts to present to your QSA. The QSA then has to review your information to develop custom testing procedures–a process that will require more reporting from the entity.
Therefore, an assessment using the Customized Approach will likely require more resources than an assessment using the defined approach, but it may be a more cost effective method when all aspects are considered. Be sure to look for a QSA with the depth and years of experience necessary to validate custom controls and develop appropriate testing procedures.
The Customized Approach method shouldn’t be a way to disengage from your assessment. Rather, utilizing the Customized Approach should encourage working closely with your QSA.
PCI DSS v4.0 may seem daunting, but it is actually an improved way to counteract the techniques used by threat actors. Preparing for compliance to v4.0 is straightforward if you are already working towards or maintaining compliance to PCI DSS 3.2.1.
As mentioned in the previous section, the Customized Approach is now available. However, before jumping right in, larger organizations and risk assessment teams may want to look at the Defined Approach and Customized Approach so that they understand the differences between the two and can make the right decisions for their organization.
A lot of people are excited about the Customized Approach because it sounds easier to get compliant. In reality, it’s going to be more complicated than it sounds. The Customized Approach requires a lot of work and effort to define what the actual requirements are and how to measure the requirements.
One of the biggest adjustments to PCI 4.0 is the increased use of risk assessments within the Customized and Defined Approaches. Risk assessments for a Customized Approach are a big part of the new standard. Instead of being a simple and quick process, organizations will need to follow a very structured formalized risk assessment.
In the past, people weren’t certain about what risk assessments were or the associated requirements. We’d often ask questions like “have you had a meeting, or have you written a document, or have you done something that shows that you’ve thought about the risks in your system?”
Now, the expectation is that if you make a change in your environment (e.g., adding a new firewall), you need to do a risk assessment on that change.
If you don’t have a lot of experience with a formal risk assessment, or don’t have a risk department as part of your company, you may need initial help from a third party to get you going and learn how to do these things.
Formal risk assessments may not seem like a big change based on some of the other future dated requirements that have been added to the standard, but this change in PCI DSS 4.0 may result in additional effort in the transition process.
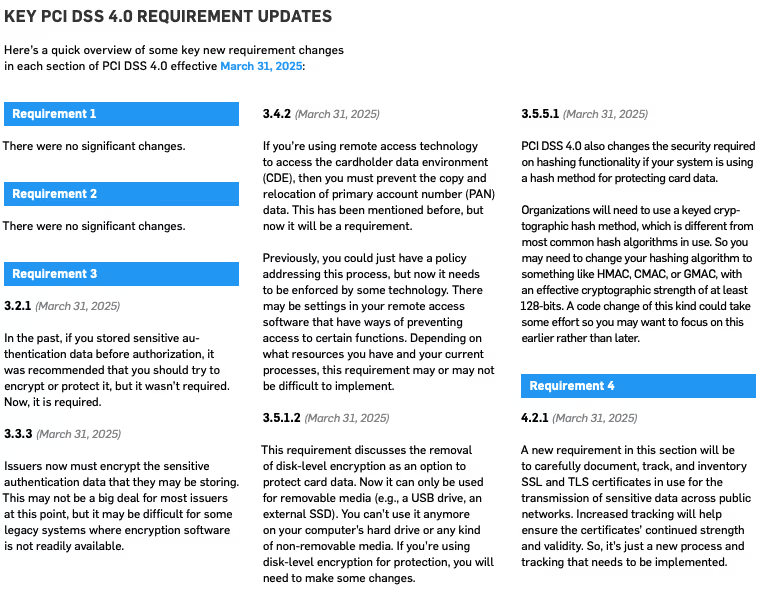
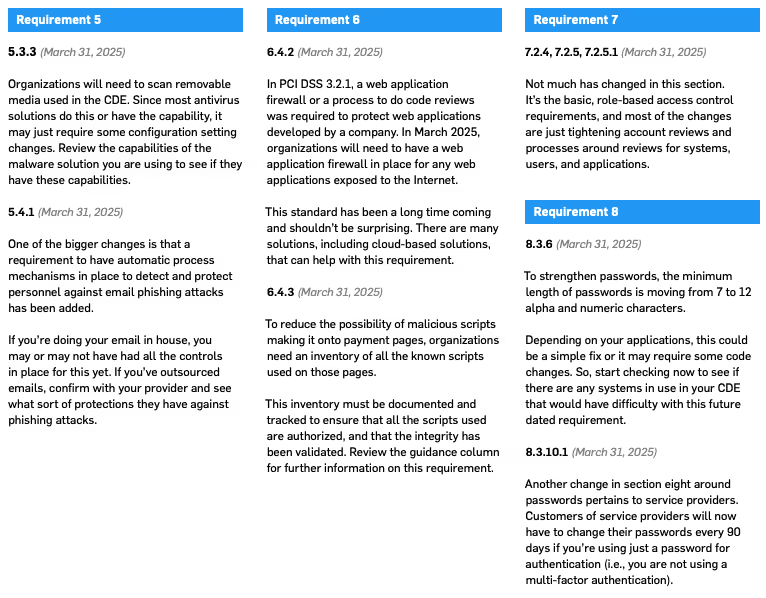
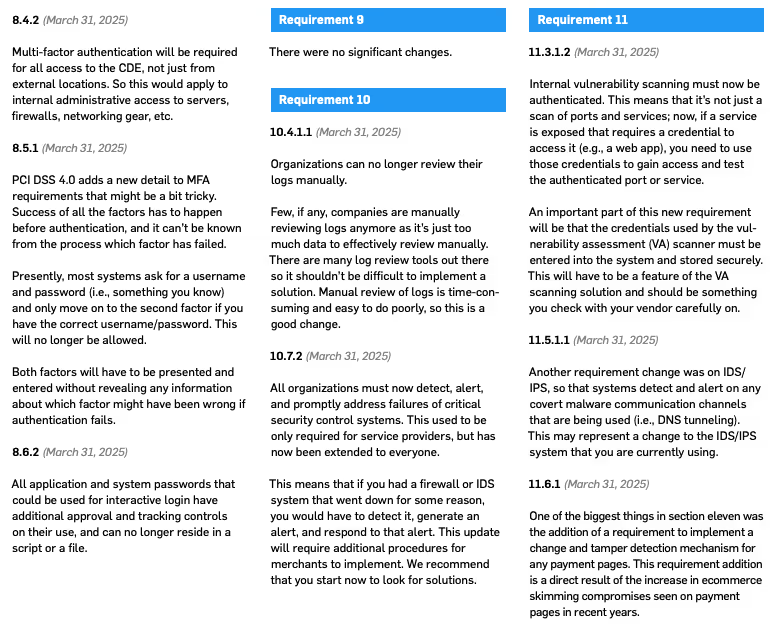
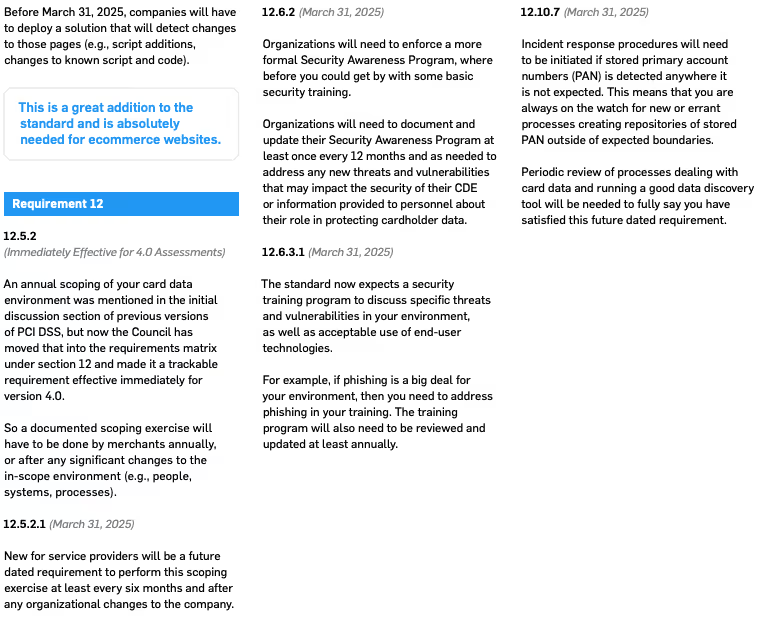
First, read the PCI DSS version 4.0 standard and get familiar with the bigger changes that could impact your compliance process. Then start formulating your plans right now to implement changes for version 4.0. There is plenty of time, so start early and you will not have problems making the transition. During this planning process don’t forget to keep working hard to keep your current efforts going to be compliant to PCI DSS version 3.2.1.
Second, start thinking about how you are conducting your risk assessments. More formal risk assessment processes are required in version 4.0 and most organizations will have to add processes and gain skills to do this correctly. Start researching formal risk assessments and refer to the industry standards out there like NIST 800-30 and OCTAVE to begin getting familiar with them. It may be a good idea to consult with a QSA as you develop these processes.
Finally, don’t wait until 2024 to begin switching over to PCI DSS 4.0. Spread your efforts across the next couple of years and you will be just fine with the new requirements.