Infographic: Cybercriminals Love When You Use Remote Access
Remote access technology has been turned against us by cybercriminals.

Remote access technology has been turned against us by cybercriminals.

Check out the infographic below for a quick overview of the remote access security problem.
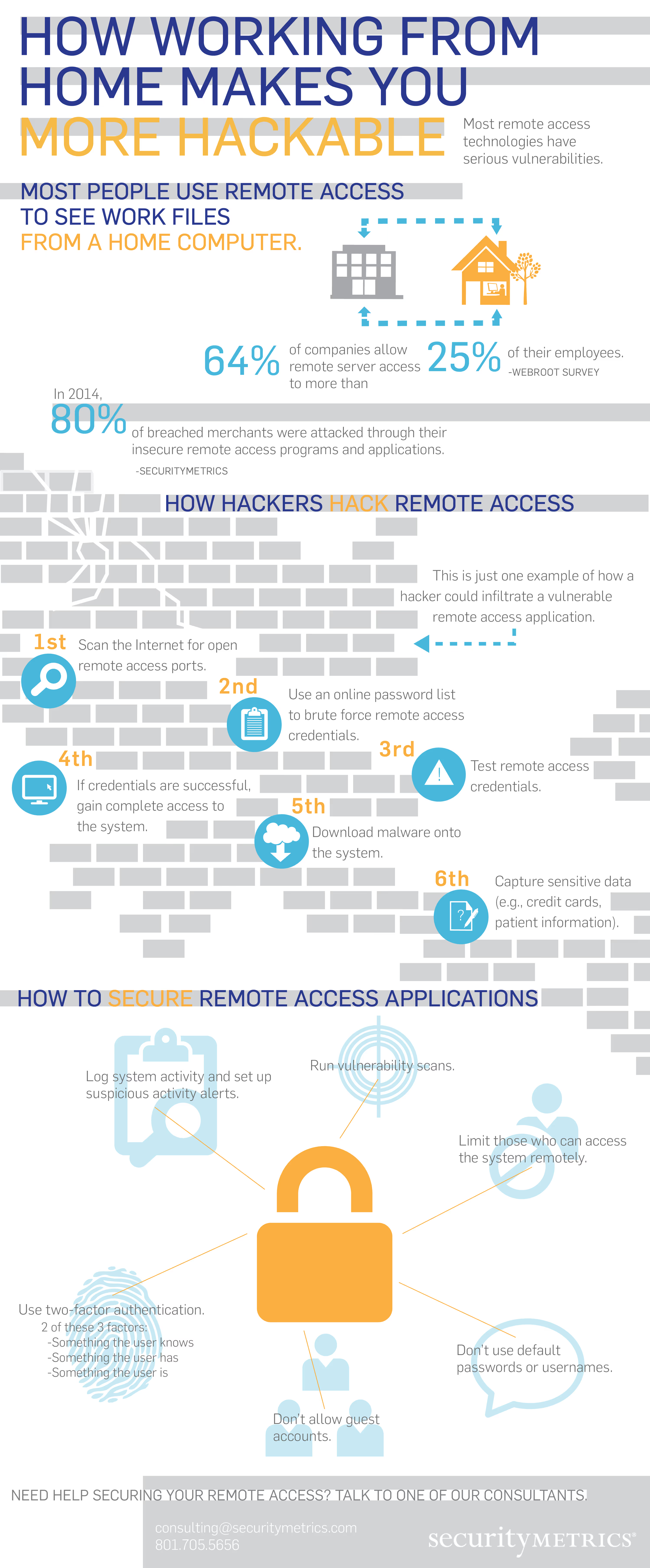
Remote computer access is one of the best ways to access work files from home, an airplane, a customer service center, an outside IT consultant, or abroad. Remote access allows a user to access a corporation’s network, and all the files, information, and sensitive data on that main corporate network, computer, or local area network.
It allows a user on one computer to see and interact with the remote system and sometimes even see the actual desktop interface of another computer without being physically present. Sometimes it's implemented using an organization’s virtual private network (VPN).
See also: SecurityMetrics PCI Guide
Remote computer access is a fantastic and very convenient technology, especially in our digital age. But there’s a problem.
Remote access technology has been turned against us by cybercriminals.
The technology we use to provide authorized access to sensitive data held by corporations has become one of the most exploited IT resources of all time.
It’s common knowledge that these applications listed above usually use these ports: 3389, 5631, 5632, 443, 80, 5900. To find a target, all a hacker has to do is scan for those specific ports to see if they’re open. An open port means remote access is used on that network.
All remote computer access applications are vulnerable to cyber attack, mostly because of the way they were configured by default. If hackers already know which ports you are using to connect with your network, all that’s left to attack are your individual credentials. All too often, these individual credentials are weak and easily guessable. Even worse, some system default passwords weren’t changed at the time of install.
I’m sure you’ve seen news stories about hackers stealing usernames and passwords to create massive libraries of billions of username/password combinations. (Did you hear about the Russian hackers who have over a billion Internet passwords?)
All it takes is a free brute force tool to automatically try each combination for them on your remote connection. There are lists published on the Internet that contain common default passwords for many types of applications, network hardware, and operating systems.
Once the hacker has successfully found the correct password/username combination, he opens the application, logs in, and uses your computer as a starting point to move throughout the entire organization.
See also: A Hacking Scenario: How Hackers Choose Their Victims
As you can see, the remote computer access problem starts with weak identity validation and authentication.
There are multiple ways to secure these applications, but the best way (by far) is implementing two-factor authentication. This means two different forms of authentication are necessary to access an application, to make sure you (and only you) get access.