Improve Your Security Posture with NIST Cybersecurity Framework
The NIST cybersecurity framework can help guide small-to-medium sized organizations improve their cybersecurity posture.
The NIST cybersecurity framework can help guide small-to-medium sized organizations improve their cybersecurity posture.

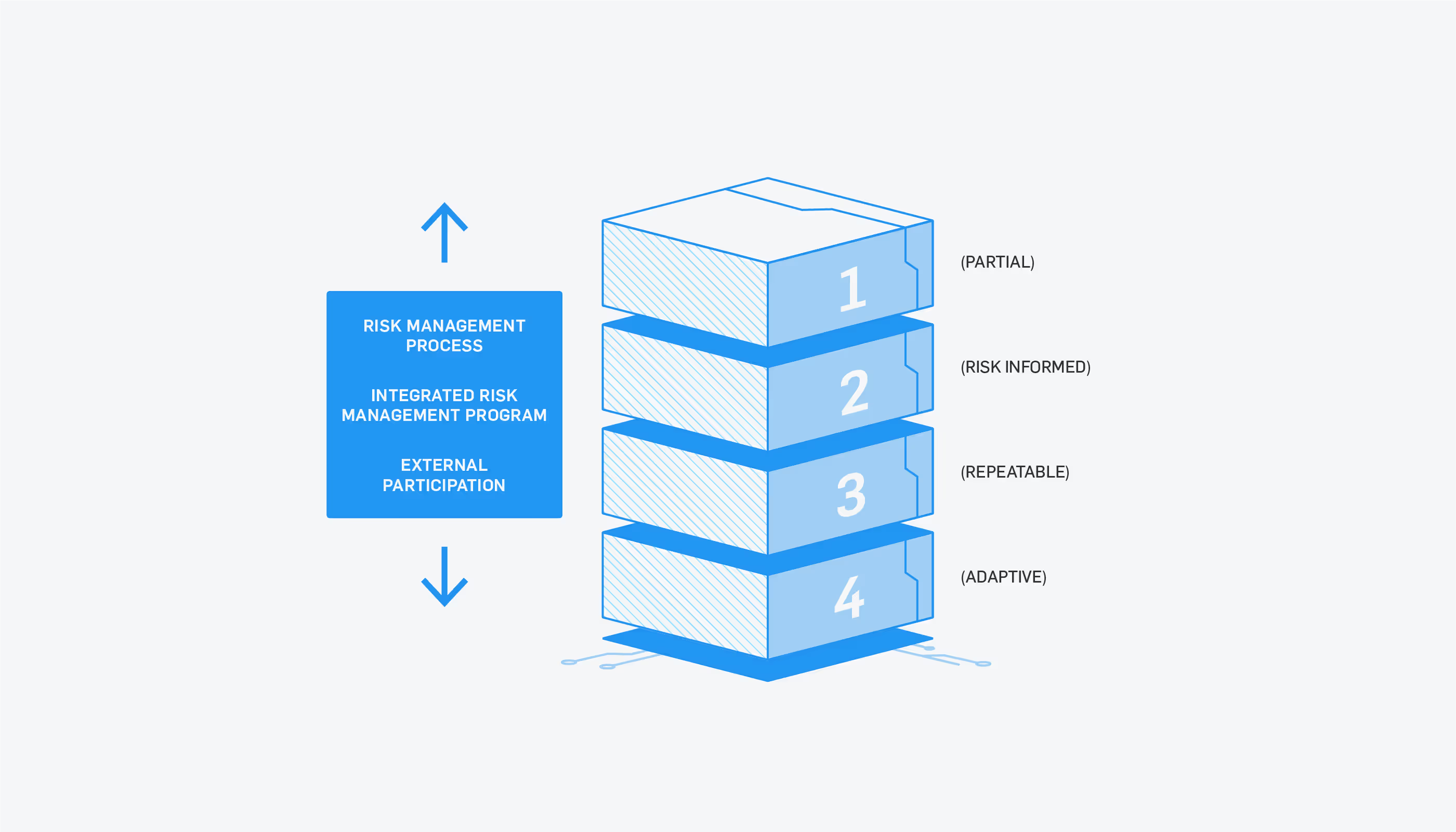
The National Institute of Standards and Technology (NIST) has provided a framework to guide small-to-medium sized organizations–including micro businesses as well as government agencies–with a set of guidelines to improve cybersecurity posture. The NIST cybersecurity framework lays out four components or “areas of focus” to identify how mature an organization’s security posture is. Addressing many of these areas of focus does not cost anything other than allocating company time.
Among the components of the NIST framework are various tiers of implementation. Each area of focus provides guidance to help you identify how mature your business is to stop threat actors in their tracks. Ideally all businesses will want to have a defense in depth approach with multiple layers of security controls.
The tiers below range from helping businesses who have very little budget, staff, or time for cyber security to more robust, adaptive approaches at large Fortune 500 organizations with huge budgets for cyber security.
You can decide for yourself which tier your business is in by reading the descriptions here or by utilizing the free NIST assessment tools provided on their site.
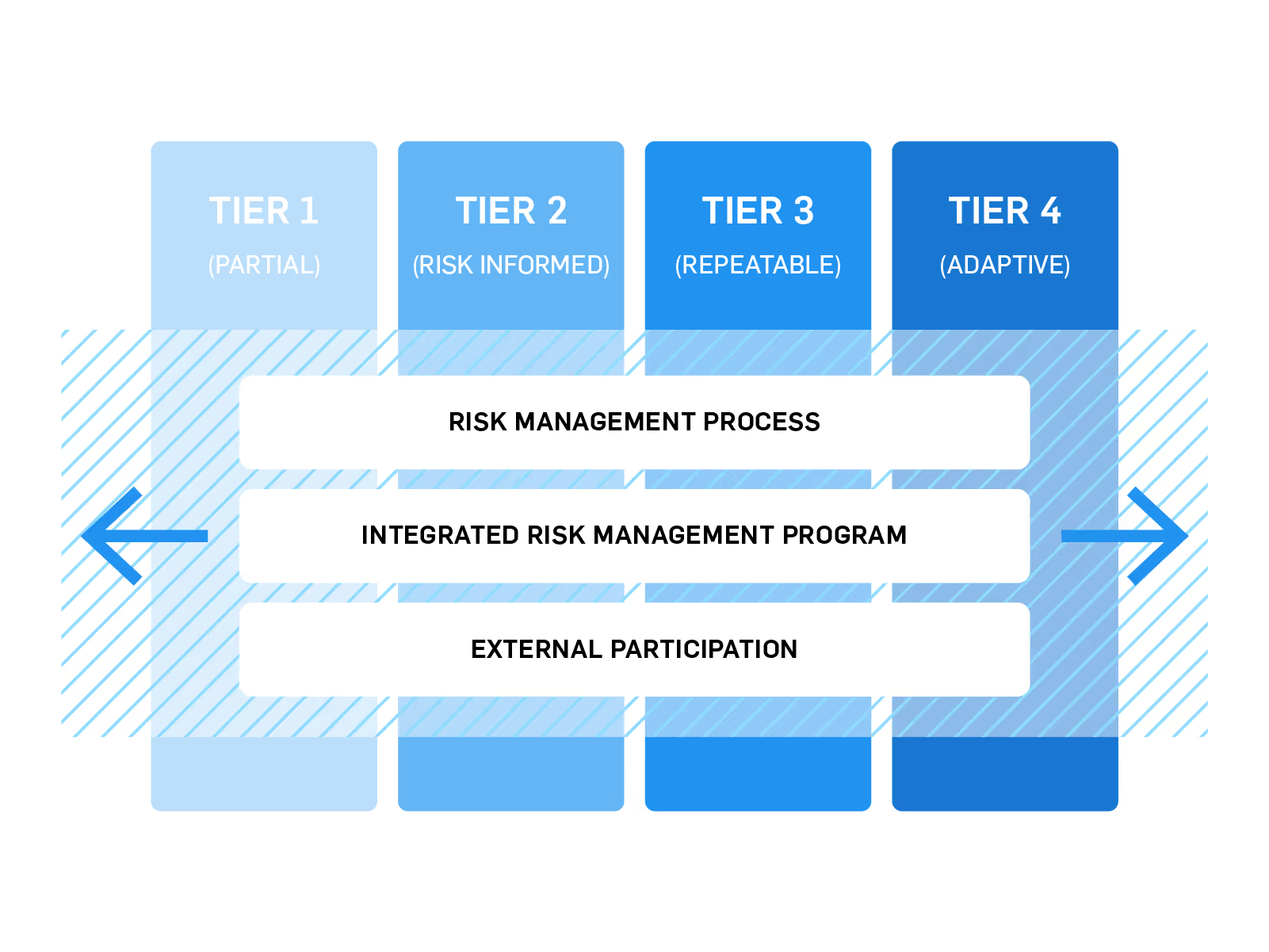
This tier covers businesses with no security processes in place. Businesses in Tier 1 are classified as not having much cyber maturity at all. Companies on this tier tend to fail at prioritizing cybersecurity settings appropriately. Companies on this level should make efforts to understand and properly address cybersecurity risks. Tier 1 is a great starting point if you don’t have a lot of time investment, staff, or budget.
This tier is for businesses that may understand risks and are currently addressing some compliance requirements; however, they may not be addressing all the security concerns or policies across the entire business. In many cases, businesses in Tier 2 are aware of some of their cybersecurity needs, but they may not address those security needs quickly enough.
Tier 3 is for businesses that have executive-approved risk management and cybersecurity best practices in place. Businesses in this category are generally more prepared for cybersecurity threats, risks, and addressing vulnerabilities in their environment. Businesses in Tier 3 spend more time collaborating with other organizations in their industry to ensure best practice alignment and benchmarking themselves against their peers.
Businesses in Tier 4 will utilize advanced adaptive cybersecurity practices. Adaptive security is an approach to cybersecurity which analyzes behaviors or events to help protect from or adapt to threats before they happen. The adaptive tier allows businesses to continuously assess risk and automatically provide proportional enforcement that can be dialed up or down based on past experiences and current industry best practices.
See also: SecurityMetrics PCI Guide
If you identified your business is in Tier 1 or 2, then you will want to start with the basics. One of the quickest, easiest areas of focus to help mature your business is security policies. You can find many templates online for writing an Information Security Policy or an Acceptable Use Policy.
Additionally, you may want to start implementing password policies such as requiring employees to use different passwords at work and home. Consider requiring all employees to use a password manager. Businesses in Tier 1 and 2 also typically offer annual or quarterly security awareness training. Employees are often the first line of defense, sometimes called the “human firewall.”
Small-to-medium businesses often use the Center for Internet Security (CIS) Top 18 Critical Security Controls as guidance or a checklist to help advance through the tiers. One important first step is to inventory all hardware and software in an environment. Anything with an IP address should be scanned and catalogued regularly. Scanning your environment can be done with many free tools found online.
If your budget permits and you want a more thorough scan, you can hire a third-party data security team to help identify many of the unknown devices or IP addresses in your business. These scanning experts specialize in very quickly auditing devices, apps, software, IoT, and cloud assets while providing your business with a prioritized list of action items that fits your IT staff capabilities and budget.
Once your inventory and auditing are complete, you can move into other areas of focus, such as securing configurations for network devices, ensuring your firewall is properly secured, hardening external devices, or controlling the use of administrative and user privileges. Maturing your cybersecurity posture can also include basic log collection to help you recover from ransomware. At a minimum, Tier 1 and 2 businesses will ensure that remote access and firewall activity is logged. They will also examine their data backup and recovery capabilities while developing an incident response plan.
There are many options to help organizations move from into Tier 1 or 2 with little investment of money or time. For example, low-cost security automation can help identify risks and vulnerabilities.
SecurityMetrics Pulse, as part of the Threat Intelligence Center (TIC), is a security automation solution which utilizes endpoints. These endpoints allow businesses to focus on their customers while the SecurityMetrics Threat Intelligence Center Team focuses on identifying malicious traffic patterns in your network. These endpoints are tiny pieces of software that look for warning signs which alert SecurityMetrics Threat Analysts where to investigate for potential breaches in your business. This is accomplished by utilizing syslog data from inside a business’s network with a combination of automated internal and external vulnerability scans.
NIST tiers are part of a framework that provides benchmark data on a business’s cybersecurity posture. There are many free NIST assessment tools to assist you in scoring your business’s cyber security posture. Once you have scored yourself, the next steps include identifying and prioritizing what you can address with your budget, staff, and available time.
SecurityMetrics offers a variety of low-investment, low-cost services and tools to help you move from one tier to the next in your cybersecurity journey. Learn more about vulnerability scanning, network security, and cybersecurity training.