Everything You Need to Know About How to Manage PHI
Fully understanding all the PHI you have, where it is stored, what processes touch it, and how it is used in your organization is critical to enabling a business to properly manage PHI.

Fully understanding all the PHI you have, where it is stored, what processes touch it, and how it is used in your organization is critical to enabling a business to properly manage PHI.

One of the first steps in protecting PHI is determining how much of it you have, what types you have, where it can be found in your organization, what systems handle it, how it is transmitted, and to whom you disclose it. You should take time to interview personnel to document those systems/processes and who has access to them.
You are probably not aware of every task and situation that your workforce members encounter daily. Interviewing personnel is one of the best ways to get further insight into how you’re interacting with and using PHI on a regular basis. It may help you discover uses, access to systems, or certain disclosures of which you were not aware.
For example, we often see large data storage areas where patient data lies around unprotected while it is “being worked on,” and staff members commonly create copies of patient data and leave the copies unattended on the printer
When IT staff don’t fully understand which system components ePHI is stored on, they don’t properly protect the data, which can and does lead to large breaches.
Fully understanding all the PHI you have, where it is stored, what processes touch it, and how it is used in your organization is critical to enabling a business to properly handle and secure PHI.
Make sure that your staff accurately understands how you use PHI/ePHI and is trained on how to properly handle it.
Detailed PHI flow diagrams (see the following examples) are vital for your risk analysis because they show how people, technology, and processes interact to create, receive, transmit, and maintain PHI. Data flow diagrams reveal where you need to focus your security efforts and training.
Begin the process by creating a diagram that shows how PHI enters your network, the systems it touches as it flows through your network, and any point at which it may leave your network.
For example, patients fill out forms at hospitals, who send patient records to doctors’ offices, who then transfer medical records to pharmacies. Or patients might add sensitive information to third-party patient portals online, which then emails a dental receptionist, who then prints and stores it in a file cabinet.
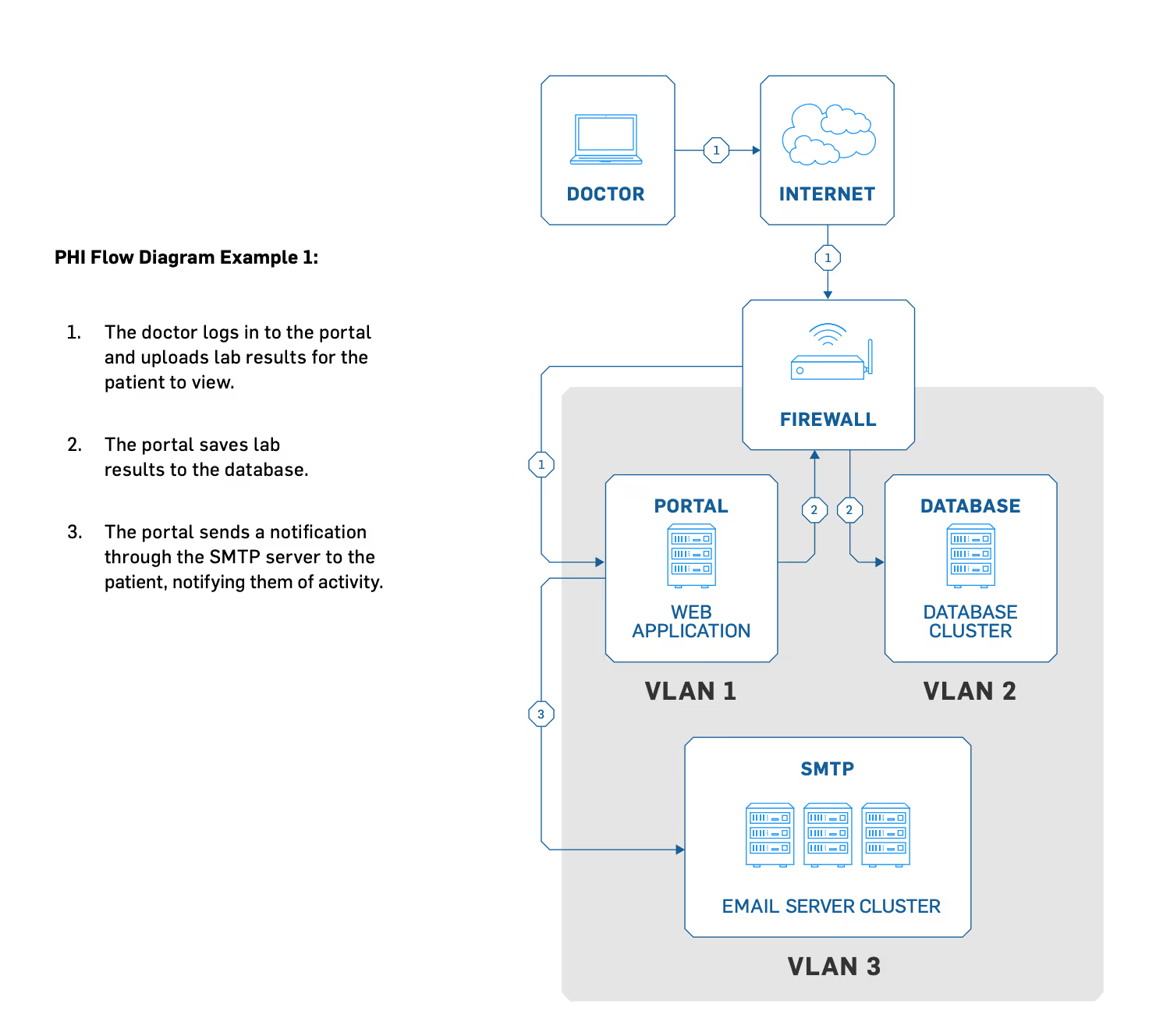
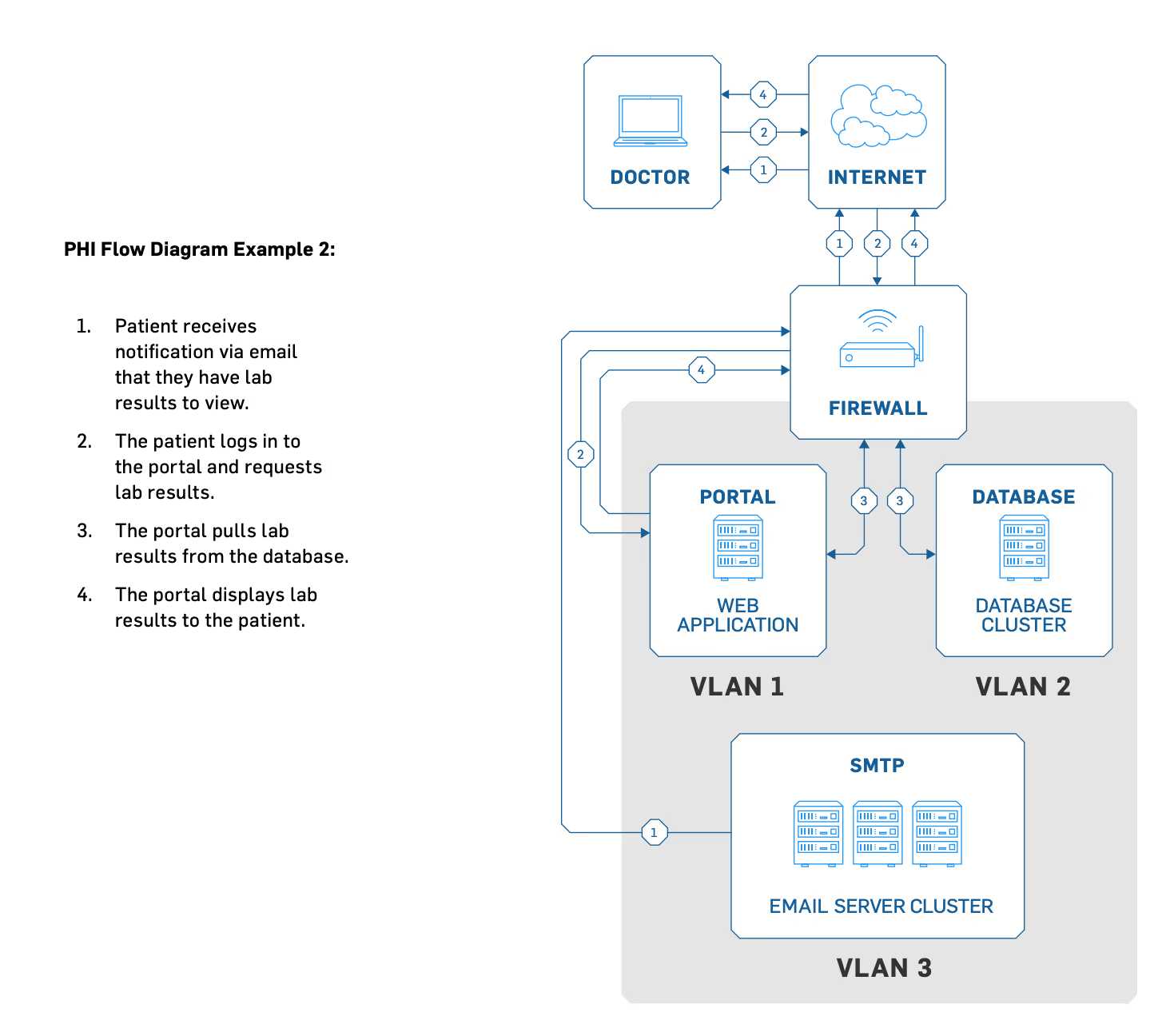
For PHI entry, think of both new and existing patient records. PHI can begin from patients filling out their own information on physical paper to the front desk taking messages for their physicians, to business associates faxing you about current or former patient information.
Consider the following sample questions when determining where your electronic PHI is created and enters your environment:
You need to know exactly what happens to PHI after it enters your environment. Is it automatically stored in your electronic health record (EHR) or electronic medical record (EMR) system? Is it copied and transferred directly to a specific department (e.g.,accounting, marketing)? Additionally, you must record all hardware, software, devices, systems, and data storage locations that can access PHI.
Here are common places PHI is stored:
When PHI leaves your organization, it’s your job to ensure PHI is transmitted or destroyed in the most secure way possible. You and your business associates are responsible for how the business associates handle your PHI.
Here are some things to consider when PHI leaves your environment:
After documenting these processes, examine them to discover gaps in your security and vulnerabilities in your environment, so you can properly secure all PHI.
As you work on your risk management plan, prioritize removing unnecessary patient data.
Before destroying old data, you’ll need to know how long you’re required to keep the data. Many states have requirements that specify the amount of time you must keep patient data. Organizations commonly maintain data for a minimum of a decade.If a patient has passed away, there will be additional requirements for data retention that must also be considered.
If you delete sensitive information (e.g., patient records, Social Security numbers), it will still be on your computer and accessible to attackers if it isn’t securely wiped. When you empty the RecycleBin or Trash, it doesn’t actually wipe the file(s) off your computer.It simply marks the file as acceptable to overwrite and is no longer visible to the user.
For the average user, these deleted files are impossible to retrieve because the operating system deletes the references to the file. While your computer can’t find that file for you anymore, that file still exists. For those with more advanced computer skills (e.g.,threat actors), this deleted data may still be accessible by looking at the unallocated disk space.
Think of the Recycle Bin or Trash like putting sensitive documents in the trash can next to your desk. Individuals could retrieve these documents if they wished; all they would need to do is pull them out of the trash can.
HHS regulations, such as 45 CFR §164.310(d)(2)(i) and (ii), states that “the HIPAA Security Rule requires that covered entities implement policies and procedures to address the final disposition of electronic PHI and/or the hardware or electronic media on which it is stored.”
HHS has determined that for electronic PHI, overwriting (i.e., using software or hardware products to overwrite media with non-sensitive data) is the best way to securely delete sensitive patient data on systems still in use.
When thinking about how to permanently delete files off your network, don’t forget about archived data, such as:
If you need to store PHI for any period of time, encrypt it. When implemented properly, encryption renders files useless to attackers because the information can’t be read without a decryption key.
HIPAA requires healthcare entities to “implement a [method] to encrypt and decrypt electronic Protected Health Information” in requirement §164.312(a)(2)(iv).12 All electronic PHI that is created, received, transmitted, and maintained in systems and on work devices (e.g., mobile phone, laptop, desktop, flash drive, hard drive)should be encrypted.
If your organization determines that encryption is not reasonable in your environment, you must document that decision and put other protections in place to protect PHI to the same degree as encryption would (or provide better protection).
As a security organization, we view encryption as critical to all PHI stored or transmitted by your organization.
As previously mentioned, you need to make sure that you map out where PHI is created, when/where it enters your environment, how/where it is stored, and what happens to it after it exits your environment or organization.
Although HIPAA regulations don’t specify the necessary encryption, industry best practice is to use these encryption types: AES-128, AES-256, or better.
Due to the complexity of encryption rules, healthcare organizations often use third parties to ensure PHI encryption. This is partly because organizations should keep decryption tools on another device or at a separate location.
Historically, one of the largest reported threats to electronic PHI has been the loss or theft of a physical device (e.g., a laptop).While employing adequate physical security and media movement procedures is the first line of defense to prevent these types of incidents, loss and theft still sometimes occur despite an organization’s best efforts.
Full disk encryption is a good way to protect your data and potentially avoid breach penalties when a device is lost or stolen.The HITECH act of 2009 modified the HIPAA Breach NotificationRule by stating that if a device is lost or stolen and it can be proven that the data is unreadable by either secure destruction or encryption, the loss is not reportable as a breach.
Full disk encryption for laptops and desktops is fairly easy to implement and usually comes with no additional cost, as most current operating systems come equipped with this capability.
According to HHS, a major goal of the Security Rule is to protect the privacy of individuals’ electronic health information, while allowing organizations to adopt new technologies to improve the quality and efficiency of patient care.
Understanding how to identify, document, store, transmit, and protect PHI is imperative to HIPAA compliance and having a solid risk management plan.
For more information on PHI, risk management plans and data security, download our free HIPAA Guide.