How Long are Businesses Vulnerable Before a Security Breach?
On average, a merchant was vulnerable for 470 days before an attacker was able to compromise the system.
On average, a merchant was vulnerable for 470 days before an attacker was able to compromise the system.

Businesses and organizations fear that dreaded data breach that could cost them millions, but how long are their systems actually vulnerable to attack?
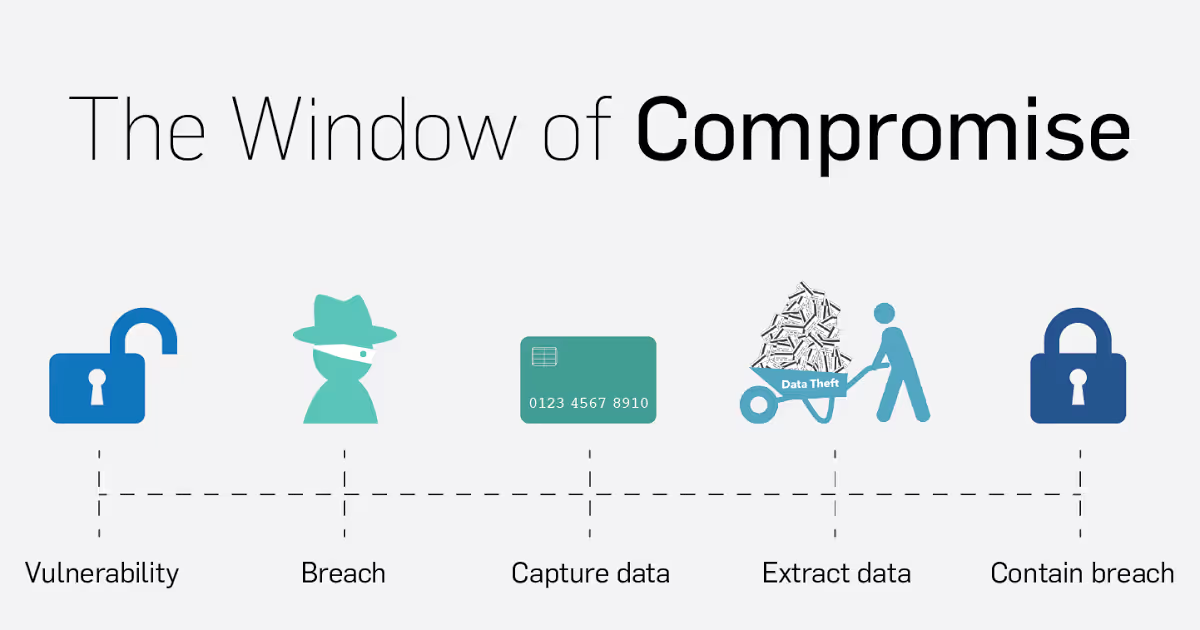
Research from SecurityMetrics states that, on average, a merchant was vulnerable for 470 days before an attacker was able to compromise the system. After compromising the system, attackers were able to capture sensitive cardholder data for an average of 176 days before the merchant discovered the vulnerability and remediated it. This chronology is known as the window of compromise.
See also: Top 5 Security Vulnerabilities Every Business Should Know
The interesting thing about the window of compromise is the fact that the average business was vulnerable for more than an entire year before a hacker came to investigate. An entire year gives any business more than adequate time to patch vulnerabilities before they are exploited. But . . . it isn’t happening.
See also: SecurityMetrics PCI Guide
Reasons that increase the likelihood of vulnerabilities include: uncompleted vulnerability scans, ignored vulnerability scan results, zero-day vulnerabilities, ineffective patching, no IT support, lack of regular environment testing, etc.
With the exception of zero-day exploits, where the vulnerability wasn’t known until the time that it was openly compromised and no patch, or “fix” was available, most other vulnerabilities that lead to data breaches could have been averted if IT security had been a higher priority. If merchants don’t conduct tests and analyses of their systems, they’re going to leave themselves open to attacks, where it’s a simple matter of time until they’re discovered.
See also: A Hacking Scenario: How Hackers Choose Their Victims
New vulnerabilities are discovered daily. A vulnerability is a system, environment, software, or website weakness that can be exploited by attackers. According to GFI, an average of 19 vulnerabilities per day were reported in 2014, totaling almost 7,000 vulnerabilities per year.
Contact us if you’re looking for a scan vendor
See also: 10 Qualities to Look For When Selecting an Approved Scanning Vendor
Creating a vulnerability management plan is crucial to decreasing a merchant’s window of vulnerability. This process will help identify, classify, remediate, and mitigate future instances of vulnerabilities. As a part of your vulnerability management strategy, include regular vulnerability scans, an annual penetration test, and the timely application of system security updates and patches. (PCI DSS compliance requires security updates within 30 days of release.)
Vigilant vulnerability management is the most efficient way for you to proactively reduce the window of compromise, greatly narrowing the opportunity for hackers to successfully attack your systems and steal your valuable data.
Read the Window of Compromise white paper.